Computer und IT

2030 - Strategieentwicklung für Innovation Leaders
Seit der Relativitätstheorie wissen wir, dass massereiche Objekte durch ihre Gravitation Dinge anziehen. Je größer die Masse desto größer ist auch die Anziehungskraft. Genauso verhält es sich auch in Strategieprojekten. Jeder Projektteilnehmer ist dabei ein massereicher Teilnehmer und hat Auswirkungen auf das Zusammenspiel. Was sich gravierend geändert hat ist der Einfluss der Daten auf diesen Prozess. Wer dies nicht berücksichtigt, wird in Zukunft enorme Einbußen hinnehmen müssen. Da sich durch diese Veränderung ein neues Gleichgewicht einstellt, ändern sich auch die Erfolgsaussichten der angewandten Methoden und Verhaltensweisen. Wie Sie diesen Wandel meistern können und was Sie dazu benötigen erfahren Sie in diesem Buch.PHILIPP FUTTERKNECHT UND TOBIAS HERTFELDER erkannten schon früh, dass man sich immer wieder neu erfinden muss, um besser zu sein als alle anderen. Seit ihren Firmengründungen perfektionieren beide ihre Methoden. Diese Erfahrungen vereinen sie nun als Digitalisierung- und Vernetzungsexperten mit hohem Managementwissen, welches sie begeistert an Menschen und Unternehmen weitergeben.Das H&F- Highspeed- und Efficiency-Konzept.-Praxisbeispiele zur Vorbeugung bekannter Stolperfallen.-Deep-Diving der Strategieerarbeitung.-Technologische Katalysatoren der Strategieumsetzung.

Beginning Windows Mixed Reality Programming
Develop applications and experiences for Microsoft’s HoloLens 2 and other Windows mixed reality devices. This easy-to-follow guide removes the mystery behind creating amazing augmented reality and virtual reality experiences. Mixed reality development tools and resources are provided.BEGINNING WINDOWS MIXED REALITY PROGRAMMING, 2ND EDITION clearly explains all the nuances of mixed reality software development. You will learn how to create 3D objects and holograms, interact with holograms using voice commands and hand gestures, use spatial mapping and 3D spatial sound, build with toolkits such as Microsoft's Mixed Reality Toolkit and Unity’s AR Foundation and XR Platform, create intuitive user interfaces, and make truly awe-inspiring mixed reality experiences. This newly revised edition also includes updated content for HoloLens 2 development, including tutorials for new interactions such as hand tracking and eye tracking.WHAT YOU WILL LEARN* Prototype ideas quickly for the HoloLens 2 and Windows mixed reality devices* Get started with Unity, the preferred tool for developing 3D experiences* Locate and import 3D models for your project, or make your own* Use spatial sound, voice commands, gestures, hand tracking, and eye tracking* Build with Microsoft's Mixed Reality Toolkit and other toolkits to make apps the easy way* Publish to the Windows Store and make money from your appWHO THIS BOOK IS FORProgrammers looking to quickly learn how to create experiences for HoloLens 2. Also for programmers interested in building applications for the growing crop of virtual reality devices that support the Windows Mixed Reality platform.SEAN ONG is an author, engineer, entrepreneur, and tech influencer who has written on topics ranging from renewable energy to augmented reality. Sean and his wife Neisha Ong founded the mixed reality development company, Ong Innovations, in 2014. Sean and his team at Ong Innovations actively work with clients and partners around the globe to push the boundaries of mixed reality and spatial computing. Sean is also co-founder of the VR telepresence robotics platform company, Laborbot, founder of the AR/VR venue-based entertainment company, Manuvr Entertainment Inc., co-founder of the AR/VR app creation platform company, Inflexion Point Inc., and serves as partner and shareholder at numerous other AR/VR startup companies around the globe. He resides in Seattle, WA with his wife and three kids, where he and his family relentlessly build the holographic future of tomorrow using today’s XR devices.PART I: GETTING STARTED1. Gear Up: The Necessary Hardware and Software Tools2. Unity Crash CoursePART II: BUILDING HOLOGRAPHIC EXPERIENCES3. Creating Your First Hologram4. Introduction to the Mixed Reality Toolkit5. Interacting with Holograms6. Using Spatial Awareness7. Spatial SoundPART III: GROWING AS A HOLOGRAPHIC DEVELOPER8. Azure Spatial Anchors9. Shared Experiences10. Awe Inspiring Experiences11. Turning Holograms into Money12. Community Resources

Explainable Natural Language Processing
THIS BOOK PRESENTS A TAXONOMY FRAMEWORK AND SURVEY OF METHODS RELEVANT TO EXPLAINING THE DECISIONS AND ANALYZING THE INNER WORKINGS OF NATURAL LANGUAGE PROCESSING (NLP) MODELS. The book is intended to provide a snapshot of Explainable NLP, though the field continues to rapidly grow. The book is intended to be both readable by first-year M.Sc. students and interesting to an expert audience. The book opens by motivating a focus on providing a consistent taxonomy, pointing out inconsistencies and redundancies in previous taxonomies. It goes on to present (i) a taxonomy or framework for thinking about how approaches to explainable NLP relate to one another; (ii) brief surveys of each of the classes in the taxonomy, with a focus on methods that are relevant for NLP; and (iii) a discussion of the inherent limitations of some classes of methods, as well as how to best evaluate them. Finally, the book closes by providing a list of resources for further research on explainability.* Introduction* A Framework for Explainable NLP* Local-Backward Explanations* Global-Backward Explanations* Local-Forward Explanations of Intermediate Representations* Global-Forward Explanations of Intermediate Representations* Local-Forward Explanations of Continuous Output* Global-Forward Explanations of Continuous Output* Local-Forward Explanations of Discrete Output* Global-Forward Explanations of Discrete Output Evaluating Explanations* Perspectives* Resources* Bibliography* Author's Biography

Basiswissen Abnahmetest
Grundlagen des Abnahmetests für Product Owner, Business-Analysten und TesterMit Abnahmetests – Acceptance Testing – wird überprüft, ob eine Software aus Sicht des Benutzers wie beabsichtigt funktioniert und dieser die Software akzeptiert.Das Buch »Basiswissen Abnahmetest« verbindet die Business-Analyse und Softwaretesten mit Blick auf die Konzepte, Methoden und Praktiken der Zusammenarbeit zwischen Business-Analysten und Testern beim Abnahmetest.Business-Analysten und Projektleiter lernen, wie sie durch die Unterstützung bei der Ausrichtung des Produkts an den Geschäftsanforderungen zu den Abnahmetestaktivitäten in einer Organisation beitragen.Tester erfahren, wie sie effizient mit Business-Analysten und anderen Stakeholdern während allen Abnahmetestaktivitäten zusammenarbeiten.Dieses Buch umfasst das erforderliche Wissen als Vorbereitung auf die Prüfung zum »Certified Tester (Foundation Level) – Acceptance Testing« nach ISTQB®-Standard. Ein durchgängiges Fallbeispiel verbindet das theoretische Wissen des Lehrplans mit dessen praktischer Anwendung beim Abnahmetest. Das Buch eignet sich damit nicht nur bestens für die Prüfungsvorbereitung, sondern dient gleichzeitig als kompaktes Basiswerk zu diesen Themen in der Praxis und an Hochschulen.Über die Autoren:Florian Fieber ist Gründer und Geschäftsführer der QualityDojo IT-Consulting GmbH in Berlin und seit knapp 15 Jahren als Berater und Trainer im Bereich der Qualitätssicherung von Softwaresystemen tätig. Seine Schwerpunkte liegen im Testmanagement, der Verbesserung von Testprozessen sowie der Businessanalyse von Enterprise-Anwendungen. Er ist Leiter der Arbeitsgruppe Acceptance Testing beim GTB (German Testing Board e.V.).Marc-Florian Wendland ist wissenschaftlicher Mitarbeiter des Geschäftsbereichs SQC (System Quality Center) im Fraunhofer Institut FOKUS in Berlin. Seine Interessen umfassen die modellgetriebene Softwareentwicklung, den automatisierten Testentwurf und Testautomatisierungsstrategien. Er ist im GTB aktiv in den Arbeitsgruppen „Testautomatisierungsentwickler“ und „Acceptance Testing“. Bei der OMG leitet er die Weiterentwicklung des UML Testing Profile (UTP).

Systematic Cloud Migration
This book is your systematic cloud migration guide. Experiences shared by the author are drawn from real-life migration projects and contain practical advice, as well as step-by-step architecture, design, and technical implementation instructions using sample application code on GitLab. Following the guidance in this book will provide much needed support to your teams, and help you successfully complete the application cloud migration journey.SYSTEMATIC CLOUD MIGRATION consists of four major parts. Part one starts with a fundamental introduction of cloud computing to establish the context for migration, including paradigm changes in five important areas: software application, DevSecOps, operations, infrastructure, and security. And these are the areas that the book follows throughout. Next, it introduces a real-life migration process that your team can follow.Part two presents the migration process for the application code, including architecture diagrams and presented by demo application code and supporting infrastructure in AWS cloud. Part three dives into DevSecOps and automation. In addition to concepts, a real-life migration diagram and sample pipeline code implemented with GitLab are include. Part four deals with efficient cloud operations.Each chapter has a practical structure: objectives, roles, inputs, process/activities, outputs/deliverables, best practices, and summary. There is a wealth of cloud production-grade template style artifacts that can be used as is.WHAT YOU WILL LEARN* Design applications in the cloud, including determining the design criteria (e.g., solution cost is a design criterion, same as security, and is not an afterthought)* Understand the major migration areas: software development (application code, data, integration, and configuration), software delivery (pipeline and automation), and software operations (observability)* Migrate each application element: client and business components code, data, integration and services, logging, monitoring, alerting, as well as configurations* Understand cloud-critical static application security testing (SAST), dynamic application security testing (DAST), containers compliance and security scanning, and open source dependency testing* Know the directions and implementation details on cost-efficient, automated, cloud-native software operationsWHO THIS BOOK IS FORPrimarily designed with software developers, team leads, development managers, DevOps engineers, and software architects in mind. Their day-to-day activities include architecting, designing, developing, delivering, and operating software in the cloud environment. In addition, this book will benefit infrastructure, network, security, and operations engineers, who in turn, can provide better support for the software development product teams.TARAS GLEB is a pragmatic and hands-on cloud solutions architect focused on software delivery, strategy, and innovation. He has been leading software development and digital transformation projects in business applications, big data, reporting, machine learning, DevSecOps, and automation. He has 25+ years of experience in design and implementation of mission-critical, customer-oriented, software solutions for institutional investors, governments, insurance companies, banks, capital markets, and power utilities. While delivering these solutions, he is applying advanced software architecture and development methodologies. His focus is on building cloud-native, secure, innovative, and cost-efficient solutions that deliver business value in an agile manner. Taras is a life-long learner who holds degrees in engineering, business administration and various industry certifications. He is continuously searching for ways to proactively apply the latest technologies and methodologies to software architecture and development.PROLOGUETARGET AUDIENCEHOW THIS BOOK IS STRUCTUREDPART I INTRODUCTION TO CLOUD COMPUTINGCHAPTER 1 TITLE: CLOUD COMPUTING PRIMER1.1 Section Title: What is Cloud Computing?1.2 Section Title: Cloud Advantages and Drawbacks1.3 Section Title: Cloud Paradigm Shifts1.4 Section Title: SummaryCHAPTER 2 TITLE: CLOUD MIGRATION FUNDAMENTALS2.1 Section Title: Cloud Organizational Structure (People)2.2 Section Title: Cloud Migration Framework (Technology)2.3 Section Title Cloud Migration Process (Process)2.4 Section Title: SummaryPART II SOFTWARE DEVELOPMENT MIGRATIONCHAPTER 3 TITLE: DEVELOP TARGET ARCHITECTURE3.1 Section Title: Input3.2 Section Title: Process & Activities3.3 Section Title: Output & Deliverables3.4 Section Title: Tools, Techniques & Best Practices3.5 Section Title: SummaryCHAPTER 4 TITLE: BUILD & SECURE CLOUD ENVIRONMENT4.1 Section Title: Input4.2 Section Title: Process & Activities4.3 Section Title: Outputs & Deliverables4.4 Best Practices, Tools & Techniques4.5 Section Title: SummaryCHAPTER 5 TITLE: MIGRATE SOFTWARE APPLICATION5.1 Section Title: Input5.2 Section Title: Process & Activities5.4 Section Title: Outputs & Deliverables5.5 Section Title: Tools, Techniques & Best PracticesBest Practices5.5 Section Title: SummaryCHAPTER 6 TITLE: ADD LOGGING MONITORING & ALERTING6.1 Section Title: Input6.2 Section Title: Process & Activities6.3 Section Title: Outputs & Deliverables6.4 Section Title: Tools, Techniques & Best PracticesBest Practices6.5 Section Title: SummaryPART III SOFTWARE DELIVERY MIGRATIONCHAPTER 7 TITLE: PROCURE SOFTWARE DELIVERY ENVIRONMENT7.1 Section Title: Input7.2 Section Title: Process & Activities7.3 Section Title: Outputs & Deliverables7.4 Section Title: Tools, Techniques & Best Practices7.5 Section Title: SummaryCHAPTER 8 TITLE: BUILD AUTOMATED PIPELINE8.1 Section Title: Input8.2 Section Title: Process & Activities8.3 Section Title: Outputs & Deliverables8.4 Section Title: Tools, Techniques & Best Practices8.5 Section Title: SummaryPART IV SOFTWARE OPERATIONS MIGRATIONCHAPTER 9 TITLE: EXECUTE FOR OPERATIONAL EXCELLENCE9.1 Section Title: Inputs9.2 Section Title: Process & Activities9.3 Section Title: Outputs & Deliverables9.4 Section Title: Tools, Techniques & Best Practices9.5 Section Title: SummaryCHAPTER 10 TITLE: TRANSITION WITH RUNBOOK & DISASTER RECOVERY10.1 Section Title: Inputs10.2 Section Title: Process & Activities10.3 Section Title: Outputs & Deliverables10.4 Section Title: Tools, Techniques & Best Practices10.5 Section Title: SummaryEPILOGUEREFERENCESAPPENDIX

Scrum-Training
Der Praxisleitfaden für Agile CoachesImmer mehr Firmen wollen zu agilen Unternehmen werden und eine »New Work«-Kultur etablieren. Das beliebte agile Rahmenwerk Scrum ist dazu oft ein wichtiger Baustein, um selbstverwaltete Teams zu etablieren. Erfolgreiche Scrum-Trainings helfen, eine agile Transformation wirksam anzustoßen, durchzuführen und insgesamt zu erleichtern.Dieses Buch bietet Ihnen als Agile Coach, Scrum Master, Trainer oder Berater einen bewährten Praxisleitfaden, um die Essenz aus Scrum interaktiv z.B. in Workshops zu vermitteln. Vielfach erprobte Übungen bieten den idealen Rahmen, damit die teilnehmenden Personen selbst zu zentralen Erkenntnissen gelangen. Der klare Tagesplan liefert dabei stets Orientierung.Doch Seminare bergen immer auch Herausforderungen. Daher werden auch der Umgang mit eher skeptischen Menschen, die Gestaltung von Lernreisen und die Steuerung von Gruppendynamik thematisiert. Durch persönliche Beispiele lebt das Autorenteam nahbar vor, wie sich eine persönliche Haltung von Agilität positiv auf das Geschehen und den Fortgang auswirkt.Nach der Lektüre des Buches wissen Sie, wie Sie ein zweitägiges Scrum-Training so aufbauen, dass dieses eine intensive und auch nachhaltige Wirkung auf alle Beteiligten entfaltet.
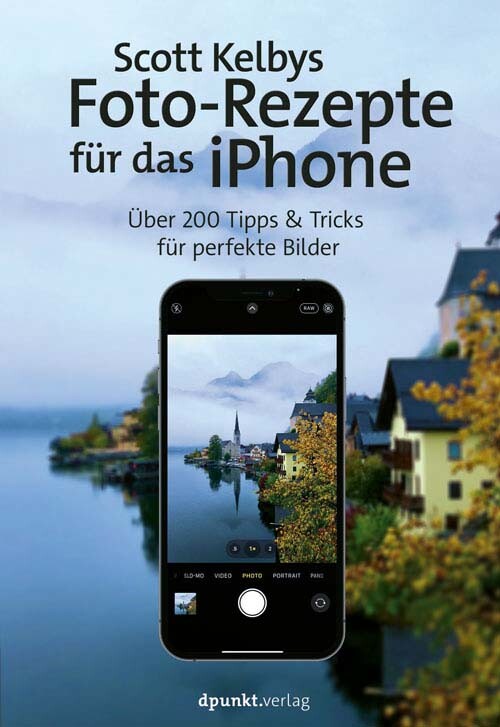
Scott Kelbys Foto-Rezepte für das iPhone
Mit der Kamera Ihres iPhones können Sie nicht nur Selfies und Schnappschüsse, sondern richtig gute Bilder machen. Perfekt komponiert und belichtet, mit Ihren Lieblingsmotiven – ob Porträts, Familie, Landschaft, Architektur, Sport, ob bei Tag oder bei Nacht.In diesem Buch erklärt Ihnen Scott Kelby in über 200 leicht verständlichen Foto-Rezepten, wie Sie die fotografischen Möglichkeiten Ihres iPhones ausschöpfen – von Technik, Bildaufbau, Licht und Posing bis zu Nachbearbeitung (mit der Lightroom-App) und Bildverwaltung (mit der Foto-App). Wichtiges Zubehör wird ausführlich in einem eigenen Kapitel erläutert, ebenso wie die besten Apps für besondere Bildbearbeitungen.

Optimizing Visual Studio Code for Python Development
Learn Visual Studio Code and implement its features in Python coding, debugging, linting, and overall project management. This book addresses custom scenarios for writing programs in Python frameworks, such as Django and Flask.The book starts with an introduction to Visual Studio Code followed by code editing in Python. Here, you will learn about the required extensions of Visual Studio Code to perform various functions such as linting and debugging in Python. Next, you will set up the environment and run your projects along with the support for Jupyter. You will also work with Python frameworks such as Django and go through data science specific-information and tutorials. Finally, you will learn how to integrate Azure for Python and how to use containers in Visual Studio Code.Optimizing Visual Studio Code for Python Development is your ticket to writing Python scripts with this versatile code editor.WHAT YOU'LL LEARN* Execute Flask development in Visual Studio Code for control over libraries used in an application* Optimize Visual Studio Code to code faster and better* Understand linting and debugging Python code in Visual Studio Code* Work with Jupyter Notebooks in Visual Studio CodeWHO THIS BOOK IS FORPython developers, beginners, and experts looking to master Visual Studio CodeSufyan bin Uzayr is a web developer with over 10 years of experience in the industry. He specializes in a wide variety of technologies, including JavaScript, WordPress, Drupal, PHP, and UNIX/Linux shell and server management, and is the author of four previous books. Sufyan is the Director of Parakozm, Kazakistan a design and development consultancy firm that offers customized solutions to a global clientele. He is also the CTO at Samurai Servers, a server management and security company catering mainly to enterprise-scale audience. He takes a keen interest in technology, politics, literature, history and sports, and in his spare time he enjoys teaching coding and English to students.OPTIMIZING VISUAL STUDIO CODE FOR PYTHON DEVELOPMENTCHAPTER ONE – INTRODUCTION TO VISUAL STUDIO CODEo Basic introduction to Visual Studio CodeCHAPTER TWO – GETTING STARTED WITH PYTHON PROGRAMS IN VS CODEo Getting started with code editingo Required extensionso Lintingo DebuggingCHAPTER THREE – SETTING UP THE ENVIRONMENT AND TESTINGo Setting up your environmento Running your projectso Support for JupyterCHAPTER FOUR – WORKING WITH PYTHON FRAMEWORKSo Django Developmento Flask Developmento Data Science specific information and tutorialsCHAPTER FIVE – WORKING WITH CONTAINERS AND MS AZUREo Integrating Azure for your Python projectso Using containers in VS Codeo Conclusion

CompTIA Network+ Study Guide
The only resource you need to prepare for the CompTIA Network+ exam CompTIA® Network+® Study Guide Fifth Edition, is your one-stop resource for the ultimate in exam preparation. Featuring 100 percent coverage of Exam N10-008 objectives, this book walks you through the essentials of network technologies, installation, configuration, media, topologies, security, and more. Networking guru Todd Lammle draws from over 30 years of networking experience to explain key topics, backed by practical examples and real-world insights relevant to what you’ll face on the job. Thanks to Sybex, you can study smarter, with well organized content, practice questions, and test-taking tips. Examples and hands-on exercises bring Network+ topics to life, so you’re confident and ready on test day! Coverage of 100% of all exam objectives in this Study Guide means you’ll be ready for: Establishing network connectivity by deploying wired and wireless devicesUnderstanding and maintaining network documentationUnderstanding the purpose of network servicesUnderstanding basic datacenter, cloud, and virtual networking conceptsMonitoring network activity, and identifying performance and availability issuesImplementing network hardening techniquesManaging, configuring, and troubleshooting network infrastructure ABOUT THE CompTIA NETWORK+ CERTIFICATION CompTIA’s Network+ is a vendor-neutral networking certification that validates the knowledge and skills to troubleshoot, configure and manage common wired and wireless networks. CompTIA Network+ is accredited by ANSI as meeting the ISO/IEC 17024 standard, and is approved by U.S. Department of Defense (DoD) to fulfill Directive 8570.01-M requirements. It is compliant with government regulations under the Federal Information Security Management Act (FISMA). Visit www.certification.comptia.org for more information. Interactive learning environment Take your exam prep to the next level with Sybex???s superior interactive online study tools. To access our learning environment, simply visit www.wiley.com/go/sybextestprep, register your book to receive your unique PIN, and instantly gain one year of FREE access after activation to: Interactive test bank with 6 practice exams help you to identify areas where further review is needed. Get more than 90% of the answers correct, and you???re ready to take the certification exam.Over 300 electronic flashcards reinforce learning and last-minute prep before the examComprehensive glossary in PDF format gives you instant access to the key terms so you are fully preparedOver 2 hours of recorded audio instruction from the author helps you study for the certification exam with confidence Prepare for the Network+ certification and a new career in network installation and administration In the newly revised Fifth Edition of CompTIA Network+ Study Guide Exam N10-008, bestselling author and network expert Todd Lammle delivers thorough coverage of how to install, configure, and troubleshoot today's basic networking hardware peripherals and protocols. This book will prepare you to succeed on the sought-after CompTIA Network+ certification exam, impress interviewers in the network industry, and excel in your first role as a junior network administrator, support technician, or related position. The accomplished author draws on his 30 years of networking experience to walk you through the ins and outs of the five functional domains covered by the Network+ Exam N10-008: Networking fundamentals, implementations, operations, security, and troubleshooting. You'll also get: Complete, domain-specific coverage of the updated Network+ Exam N10-008Preparation to obtain a leading network certification enjoyed by over 350,000 networking professionalsAccess to Sybex's superior set of online study tools, including practice exams, flashcards, and glossary of key terms, all supported by Wiley's support agents who are available 24x7 via email or live chat to assist with access and login questions Perfect for anyone preparing for the latest version of the CompTIA Network+ Exam N10-008, the Fifth Edition of CompTIA Network+ Study Guide Exam N10-008 is a must-have resource for network administrators seeking to enhance their skillset with foundational skills endorsed by industry and thought leaders from around the world. Introduction xxxi Assessment Test xli Chapter 1 Introduction to Networks 1 First Things First: What’s a Network? 3 The Local Area Network 4 Common Network Components 6 Metropolitan Area Network 9 Wide Area Network 9 Personal Area Network 10 Campus Area Network 10 Storage Area Network 10 Software-Defined Wide Area Network 11 Multiprotocol Label Switching 11 Multipoint Generic Routing Encapsulation 12 Network Architecture: Peer-to-Peer or Client-Server? 12 Physical Network Topologies 14 Bus Topology 14 Star Topology 15 Ring Topology 17 Mesh Topology 17 Point-to-Point Topology 18 Point-to-Multipoint Topology 19 Hybrid Topology 20 Topology Selection, Backbones, and Segments 21 Selecting the Right Topology 22 The Network Backbone 22 Network Segments 23 Service-Related Entry Points 23 Service Provider Links 23 Virtual Networking 24 Summary 24 Exam Essentials 25 Written Lab 25 Review Questions 26 Chapter 2 The Open Systems Interconnection Specifications 31 Internetworking Models 32 The Layered Approach 33 Advantages of Reference Models 33 The OSI Reference Model 34 The Application Layer 36 The Presentation Layer 37 The Session Layer 37 The Transport Layer 37 The Network Layer 43 The Data Link Layer 46 The Physical Layer 48 Introduction to Encapsulation 49 Modulation Techniques 50 Summary 51 Exam Essentials 51 Written Lab 52 Review Questions 53 Chapter 3 Networking Connectors and Wiring Standards 57 Physical Media 59 Coaxial Cable 60 Twisted-Pair Cable 62 Twinaxial Cable 62 Fiber-Optic Cable 66 Transceivers 71 Media Converters 72 Serial Cables 74 Cable Properties 76 Transmission Speeds 76 Distance 76 Duplex 77 Noise Immunity (Security, EMI) 77 Frequency 77 Wiring Standards 78 T568A vs. T568B 78 Straight-Through Cable 80 Crossover Cable 81 Rolled/Rollover Cable 83 T1 Crossover Cable 83 Installing Wiring Distributions 85 MDF/IDF 85 Summary 87 Exam Essentials 88 Written Lab 88 Review Questions 89 Chapter 4 The Current Ethernet Specifications 93 Network Basics 94 Ethernet Basics 96 Collision Domain 96 Broadcast Domain 97 CSMA/CD 97 Broadband/Baseband 99 Bit Rates vs. Baud Rate 99 Wavelength 99 Half-and Full-Duplex Ethernet 100 Ethernet at the Data Link Layer 102 Binary to Decimal and Hexadecimal Conversion 102 Ethernet Addressing 106 Ethernet Frames 107 Ethernet at the Physical Layer 109 Ethernet over Other Standards (IEEE 1905.1-2013) 115 Ethernet over Power Line 115 Ethernet over HDMI 117 Bidirectional Wavelength-Division Multiplexing (WDM) 117 Course Wavelength-Division Multiplexing (CWDM) 117 Dense Wavelength-Division Multiplexing (DWDM) 117 Summary 118 Exam Essentials 119 Written Lab 119 Review Questions 124 Chapter 5 Networking Devices 129 Common Network Connectivity Devices 132 Network Interface Card 133 Hub 135 Bridge 135 Switch 136 Router 137 Firewall 141 IDS/IPS 142 HIDS 142 Access Point 142 Wireless Range Extender 143 Wireless LAN Controller 143 Load Balancer 144 Contention Methods 144 Dynamic Host Configuration Protocol Server 147 IPAM 152 Other Specialized Devices 152 Multilayer Switch 153 Domain Name Service Server 153 Network Time Protocol 160 Proxy Server 160 Encryption and Content Filtering 162 Analog Modem 163 Packet Shaper 164 VPN Concentrator/Headend 164 Media Converter 165 VoIP PBX 165 VoIP Endpoint 166 NGFW/Layer 7 Firewall 166 VoIP Gateway 166 Cable Modem 166 DSL Modem 166 Networked Devices 167 VoIP Phones 167 Printers 167 Physical Access Control Devices 167 Cameras 167 Heating Ventilation, and Air Conditioning (HVAC) Sensors 167 Internet of Things (IoT) 168 Industrial Control Systems 168 Planning and Implementing a Basic SOHO Network Using Network Segmentation 168 Determining Requirements 169 Switches and Bridges at the Data Link Layer 175 Hubs at the Physical Layer 177 Environmental Considerations 178 Summary 178 Exam Essentials 179 Written Lab 180 Review Questions 181 Chapter 6 Introduction to the Internet Protocol 185 Introducing TCP/IP 188 A Brief History of TCP/IP 188 TCP/IP and the DoD Model 189 The Process/Application Layer Protocols 191 The Host-to-Host Layer Protocols 204 The Internet Layer Protocols 210 Data Encapsulation 220 Summary 224 Exam Essentials 224 Written Lab 225 Review Questions 226 Chapter 7 IP Addressing 231 IP Terminology 233 The Hierarchical IP Addressing Scheme 234 Network Addressing 235 Private IP Addresses (RFC 1918) 239 IPv4 Address Types 241 Layer 2 Broadcasts 242 Layer 3 Broadcasts 242 Unicast Address 243 Multicast Address (Class D) 243 Internet Protocol Version 6 (IPv6) 243 Why Do We Need IPv6? 244 The Benefits of and Uses for IPv6 244 IPv6 Addressing and Expressions 246 Shortened Expression 246 Address Types 247 Special Addresses 248 Stateless Address Autoconfiguration (SLAAC) 249 DHCPv6 (Stateful) 251 Migrating to IPv6 251 Summary 253 Exam Essentials 254 Written Labs 255 Written Lab 7.1 255 Written Lab 7.2 255 Review Questions 257 Chapter 8 IP Subnetting, Troubleshooting IP, and Introduction to NAT 261 Subnetting Basics 263 How to Create Subnets 264 Subnet Masks 265 Classless Inter-Domain Routing (CIDR) 266 Subnetting Class C Addresses 268 Subnetting Class B Addresses 278 Troubleshooting IP Addressing 286 Determining IP Address Problems 289 Introduction to Network Address Translation (NAT) 294 Types of Network Address Translation 295 NAT Names 295 How NAT Works 296 Summary 298 Exam Essentials 298 Written Lab 299 Review Questions 300 Chapter 9 Introduction to IP Routing 305 Routing Basics 306 The IP Routing Process 309 Testing Your IP Routing Understanding 315 Static and Dynamic Routing 316 Summary 319 Exam Essentials 319 Written Lab 320 Review Questions 321 Chapter 10 Routing Protocols 325 Routing Protocol Basics 326 Administrative Distances 327 Classes of Routing Protocols 329 Distance-Vector Routing Protocols 330 Routing Information Protocol (RIP) 332 RIP Version 2 (RIPv2) 332 VLSMs and Discontiguous Networks 333 EIGRP 336 Border Gateway Protocol (BGP) 338 Link-State Routing Protocols 340 Open Shortest Path First (OSPF) 340 Intermediate System-to-Intermediate System (IS-IS) 343 High Availability 344 Hot Standby Router Protocol (HSRP) 346 Virtual Router Redundancy Protocol 350 Advanced IPv6 Concepts 351 Router Advertisement 351 Neighbor Discovery Protocol 353 Tunneling 354 Dual Stack 357 IPv6 Routing Protocols 357 RIPng 358 EIGRPv6 358 OSPFv3 359 Summary 359 Exam Essentials 359 Written Lab 360 Review Questions 361 Chapter 11 Switching and Virtual LANs 365 Networking Before Layer 2 Switching 367 Switching Services 370 Limitations of Layer 2 Switching 371 Bridging vs. LAN Switching 372 Three Switch Functions at Layer 2 372 Distributed Switching 378 Spanning Tree Protocol 378 Spanning Tree Port States 379 STP Convergence 380 Rapid Spanning Tree Protocol 802.1w 381 Virtual LANs 382 VLAN Basics 383 Quality of Service 386 VLAN Memberships 387 Static VLANs 387 Dynamic VLANs 388 Identifying VLANs 388 VLAN Identification Methods 390 VLAN Trunking Protocol 392 VTP Modes of Operation 393 Do We Really Need to Put an IP Address on a Switch? 394 Switch Port Protection 396 Port Bonding 399 Device Hardening 401 Two Additional Advanced Features of Switches 401 Power over Ethernet (802.3af, 802.3at) 401 Port Mirroring/Spanning (SPAN/RSPAN) 404 Summary 405 Exam Essentials 406 Written Lab 406 Review Questions 408 Chapter 12 Wireless Networking 413 Introduction to Wireless Technology 415 Cellular Technologies 418 The 802.11 Standards (Regulatory Impacts) 419 2.4 GHz (802.11b) 421 2.4 GHz (802.11g) 422 5 GHz (802.11a) 423 5 GHz (802.11h) 424 2.4 GHz/5 GHz (802.11n) 425 5 GHz (802.11ac) 426 WiFi 6 (802.11ax) 426 Comparing 802.11 Standards 427 Range and Speed Comparisons 428 Wireless Network Components 428 Wireless Access Points 429 Wireless Network Interface Card 430 Wireless Antennas 431 Installing a Wireless Network 432 Ad Hoc Mode: Independent Basic Service Set 432 Infrastructure Mode: Basic Service Set 433 Wireless Controllers 434 Mobile Hot Spots 436 Signal Degradation 438 Other Network Infrastructure Implementations 438 Technologies That Facilitate the Internet of Things (IoT) 440 Installing and Configuring WLAN Hardware 441 Site Survey 447 Providing Capacity 448 Multiple Floors 449 Location-Based WLAN 450 Site Survey Tools 450 Wireless Security 451 Wireless Threats 451 Open Access 455 Service Set Identifiers, Wired Equivalent Privacy, and Media Access Control Address Authentication 455 Remote Authentication Dial-In User Service (802.1X) 457 Temporal Key Integrity Protocol 458 Wi-Fi Protected Access or WPA2 Pre-Shared Key 459 Summary 462 Exam Essentials 462 Written Lab 464 Review Questions 465 Chapter 13 Using Statistics and Sensors to Ensure Network Availability 469 Performance Metrics/Sensors 471 Device/Chassis 471 Network Metrics 473 SNMP 474 Traps 475 Object Identifiers (OIDs) 476 Management Information Bases (MIBs) 476 Network Device Logs 476 Log Reviews 476 Logging Levels/Severity Levels 480 Interface Statistics/Status 482 Link State (Up/Down) 482 Speed/Duplex 483 Send/Receive Traffic 484 Cyclic Redundancy Checks (CRCs) 485 Protocol Packet and Byte Counts 486 Interface Errors or Alerts 486 CRC Errors 487 Giants and Runts 488 Encapsulation Errors 488 Environmental Factors and Sensors 489 Temperature 489 Humidity 489 Electrical 490 Flooding 495 Baselines 495 NetFlow Data 496 NetFlow Overview and Flows 496 Uptime/Downtime 498 Summary 498 Exam Essentials 498 Written Lab 499 Review Questions 501 Chapter 14 Organizational Documents and Policies 505 Plans and Procedures 507 Change Management 508 Incident Response Plan 510 Disaster Recovery Plan 510 Business Continuity Plan 510 System Life Cycle 511 Standard Operating Procedures 511 Hardening and Security Policies 511 Acceptable Use Policy 512 Password Policy 512 Bring Your Own Device (BYOD) Policy 513 Remote Access Policy 513 Onboarding and Offboarding Policy 513 Security Policy 514 Data Loss Prevention 519 Common Documentation 519 Physical Network Diagram 520 Logical Network Diagram 524 Wiring Diagram 525 Site Survey Report 526 Audit and Assessment Report 526 Baseline Configurations 527 Common Agreements 528 Nondisclosure Agreement (NDA) 528 Service-Level Agreement (SLA) 529 Memorandum of Understanding (MOU) 529 Summary 529 Exam Essentials 529 Written Lab 530 Review Questions 531 Chapter 15 High Availability and Disaster Recovery 533 Load Balancing 535 Multipathing 536 Network Interface Card (NIC) Teaming 537 Redundant Hardware/Clusters 538 Switches 538 Routers 540 Firewalls 542 Facilities and Infrastructure Support 542 Uninterruptible Power Supply (UPS) 542 Power Distribution Units (PDUs) 543 Generator 543 HVAC 544 Fire Suppression 544 Redundancy and High Availability (HA) Concepts 545 Recovery Sites 545 Cold Site 545 Warm Site 545 Hot Site 546 Cloud Site 546 Active/Active vs. Active/Passive 546 Mean Time to Repair (MTTR) 553 Mean Time Between Failure (MTBF) 554 Recovery Time Objective (RTO) 554 Recovery Point Objective (RPO) 554 Network Device Backup/Restore 554 State/Configuration 554 Summary 555 Exam Essentials 555 Written Lab 556 Review Questions 557 Chapter 16 Common Security Concepts 559 Confidentiality, Integrity, and Availability (CIA) 561 Confidentiality 561 Integrity 561 Availability 562 Threats 562 Internal 562 External 562 Vulnerabilities 562 Common Vulnerabilities and Exposures (CVE) 563 Zero-Day 563 Exploits 563 Least Privilege 563 Role-Based Access 564 Zero Trust 564 Defense in Depth 564 Network Segmentation Enforcement 564 Screened Subnet (aka Demilitarized Zone) 565 Separation of Duties 565 Network Access Control 566 Honeypot 567 Authentication Methods 567 Multifactor 567 Authentication, Authorization, and Accounting (AAA) 568 Remote Authentication Dial-In User Service (RADIUS) 568 Terminal Access Controller Access Control System Plus (TACACS+) 568 Single Sign-On (SSO) 570 LDAP 570 Kerberos 570 Local Authentication 571 802.1X 571 Extensible Authentication Protocol (EAP) 572 Security Risk Assessments 573 Threat Assessment 573 Vulnerability Assessment 574 Penetration Testing 575 Business Risk Assessments 575 Security Information and Event Management (SIEM) 576 Notifications 576 Summary 576 Exam Essentials 577 Written Lab 577 Review Questions 578 Chapter 17 Common Types of Attacks 581 Technology-Based Attacks 582 Denial of Service (DoS)/Distributed Denial of Service (DDoS) 583 On-Path Attack (Previously Known as Man-in-the-Middle Attack) 588 DNS Poisoning 589 VLAN Hopping 589 ARP Spoofing 590 Rogue DHCP 590 Rogue Access Point (AP) 591 Evil Twin 592 Ransomware 593 Password Attacks 593 MAC Spoofing 594 IP Spoofing 594 Deauthentication 594 Malware 594 Human and Environmental 598 Social Engineering 598 Phishing 599 Environmental 599 Summary 600 Exam Essentials 600 Written Lab 601 Review Questions 602 Chapter 18 Network Hardening Techniques 605 Best Practices 607 Secure SNMP 608 Router Advertisement (RA) Guard 608 Port Security 608 Dynamic ARP Inspection 609 Control Plane Policing 609 Private VLANs 609 Disable Unneeded Switchports 610 Disable Unneeded Network Services 610 Change Default Passwords 610 Password Complexity/Length 610 Enable DHCP Snooping 613 Change Default VLAN 613 Patch and Firmware Management 614 Access Control List 615 Role-Based Access 616 Firewall Rules 617 Wireless Security 618 MAC Filtering 618 Antenna Placement 618 Power Levels 619 Wireless Client Isolation 619 Guest Network Isolation 620 Preshared Keys (PSKs) 620 EAP 620 Geofencing 620 Captive Portal 621 IoT Access Considerations 621 Summary 621 Exam Essentials 621 Written Lab 622 Review Questions 623 Chapter 19 Remote Access Security 625 Site-to-Site VPN 626 Client-to-Site VPN 626 Clientless VPN 627 Split Tunnel vs. Full Tunnel 628 Remote Desktop Connection 628 Remote Desktop Gateway 629 SSH 630 Virtual Network Computing (VNC) 630 Virtual Desktop 631 Authentication and Authorization Considerations 631 In-Band vs. Out-of-Band Management 631 Summary 632 Exam Essentials 632 Written Lab 632 Review Questions 634 Chapter 20 Physical Security 637 Detection Methods 639 Cameras 639 Motion Detection 640 Asset Tags 641 Tamper Detection 641 Prevention Methods 642 Employee Training 642 Access Control Hardware 643 Locking Racks 643 Locking Cabinets 644 Access Control Vestibule (Previously Known as a Mantrap) 644 Smart Lockers 645 Asset Disposal 646 Factory Reset/Wipe Configuration 646 Sanitize Devices for Disposal 646 Summary 647 Exam Essentials 647 Written Lab 648 Review Questions 649 Chapter 21 Data Center Architecture and Cloud Concepts 651 Data Center Network Architectures 654 Access/Edge Layer 654 Distribution Layer 655 Core Layer 655 Software-Defined Networking 655 Application Layer 656 Control Layer 656 Infrastructure Layer 656 Management Plane 656 Spine-Leaf–Based Two-Tier Networks 657 Top-of-Rack Switching 658 Backbone 658 Traffic Flows 658 North-South 659 East-West 659 Branch Office vs. On-premises Data Center vs. Colocation 660 Cloud Computing and Its Effect on the Enterprise Network 661 Service Models 663 Overview of Network Programmability in Enterprise Network 665 Software-Defined Networking 666 Application Programming Interfaces (APIs) 666 Southbound APIs 667 Northbound APIs 669 Managing Network Documentation 670 Using SNMP 670 Schematics and Diagrams 671 Network Monitoring 676 Baselines 676 Processes 676 Onboarding and Offboarding of Mobile Devices 677 NAC 677 Policies, Procedures, and Regulations 677 Safety Practices 681 Implementing Network Segmentation 686 Network Optimization 689 Reasons to Optimize Your Network’s Performance 689 How to Optimize Performance 691 Unified Communications 694 Traffic Shaping 694 Load Balancing 695 High Availability 695 Caching Engines 695 Fault Tolerance 696 Archives/Backups 696 Common Address Redundancy Protocol 697 Virtual Networking 697 Locating and Installing Equipment 708 Change Management Procedures 715 Summary 717 Exam Essentials 719 Written Lab 720 Review Questions 721 Chapter 22 Ensuring Network Availability 725 Performance Metrics/Sensors 727 Network Metrics 728 SNMP 729 Network Device Logs 731 Interface Statistics/Status 733 Interface Errors 734 Environmental Factors and Sensors 735 Baseline 736 NetFlow 737 Uptime 738 Downtime 738 Summary 739 Exam Essentials 739 Written Lab 740 Review Questions 741 Chapter 23 Cable Connectivity Issues and Tools 745 Specifications and Limitations 747 Cable Considerations 747 Cable Applications 748 Common Issues 749 Identifying Hardware Tools 751 Cable Testers 752 Protocol Analyzer 755 Certifiers 755 Time-Domain Reflectometer 756 Optical Time-Domain Reflectometer 756 Multimeter 757 Spectrum Analyzer 758 Toner Generator (Probe) 759 Tap 760 Metrics 760 Butt Set 761 Punch-Down Tool 761 Cable Snips/Cutters 763 Voltage Event Recorder (Power) 763 Fiber Light Meter 764 Fiber Fusion Splicer 764 Summary 765 Exam Essentials 765 Written Lab 766 Review Questions 767 Chapter 24 Network Troubleshooting Methodology 771 Narrowing Down the Problem 775 Did You Check the Super Simple Stuff? 776 Is Hardware or Software Causing the Problem? 780 Is It a Workstation or a Server Problem? 781 Which Segments of the Network Are Affected? 781 Is It Bad Cabling? 782 Troubleshooting Steps 791 Step 1: Identify the Problem 792 Step 2: Establish a Theory of Probable Cause 796 Step 3: Test the Theory to Determine Cause 806 Step 4: Establish a Plan of Action to Resolve the Problem and Identify Potential Effects 809 Step 5: Implement the Solution or Escalate as Necessary 810 Step 6: Verify Full System Functionality, and If Applicable, Implement Preventative Measures 813 Step 7: Document Findings, Actions, Outcomes, and Lessons Learned 814 Troubleshooting Tips 815 Don’t Overlook the Small Stuff 815 Prioritize Your Problems 815 Check the Software Configuration 816 Don’t Overlook Physical Conditions 817 Don’t Overlook Cable Problems 817 Check for Viruses 818 Summary 818 Exam Essentials 818 Written Lab 819 Review Questions 821 Chapter 25 Network Software Tools and Commands 825 Software Tools 827 Wi-Fi Analyzers 827 Protocol Analyzer/Packet Capture 828 Bandwidth Speed Testers 829 Port Scanners 830 NetFlow Analyzers 830 Trivial File Transfer Protocol (TFTP) Server 831 Connectivity Software 831 IP Scanner 832 Using traceroute 833 Using ipconfig, ifconfig, and ip 836 Using the ipconfig Utility 836 Using the ifconfig Utility 840 Using the ip Utility 840 Using the iptables Utility 841 Examples of iptables 841 Using the ping Utility 841 Using the Address Resolution Protocol 845 The Windows ARP Table 845 Using the arp Utility 846 Using the nslookup Utility 849 Resolving Names with the Hosts File 850 Using the Mtr Command (pathping) 852 Using the Nmap Utility 853 Using the route Command 854 Using the route Command Options 854 Some Examples of the route Command 857 Using the nbtstat Utility 857 The –a Switch 858 The –A Switch 860 The –c Switch 860 The –n Switch 860 The –r Switch 861 The –R Switch 862 The –S Switch 862 The –s Switch 863 Using the netstat Utility 863 The –a Switch 866 The –e Switch 866 The –r Switch 867 The –s Switch 867 The –p Switch 868 The –n Switch 869 Using tcpdump 871 Examples of Using tcpdump 871 Using the File Transfer Protocol 871 Starting FTP and Logging In to an FTP Server 872 Downloading Files 874 Uploading Files 876 Using the Telnet Utility 876 How to Enable Telnet in Windows 877 Don’t Use Telnet, Use Secure Shell 878 Summary 878 Exam Essentials 879 Written Lab 880 Review Questions 881 Appendix A Answers to Written Labs 887 Chapter 1: Introduction to Networks 888 Chapter 2: The Open Systems Interconnection Specifications 888 Chapter 3: Networking Connectors and Wiring Standards 889 Chapter 4: The Current Ethernet Specifications 889 Chapter 5: Networking Devices 891 Chapter 6: Introduction to the Internet Protocol 892 Chapter 7: IP Addressing 893 Written Lab 7.1 893 Written Lab 7.2 893 Chapter 8: IP Subnetting, Troubleshooting IP, and Introduction to NAT 894 Chapter 9: Introduction to IP Routing 895 Chapter 10: Routing Protocols 895 Chapter 11: Switching and Virtual LANs 895 Chapter 12: Wireless Networking 896 Chapter 13: Using Statistics and Sensors to Ensure Network Availability 896 Chapter 14: Organizational Documents and Policies 897 Chapter 15: High Availability and Disaster Recovery 898 Chapter 16: Common Security Concepts 898 Chapter 17: Common Types of Attacks 899 Chapter 18: Network Hardening Techniques 899 Chapter 19: Remote Access Security 900 Chapter 20: Physical Security 900 Chapter 21: Data Center Architecture and Cloud Concepts 901 Chapter 22: Ensuring Network Availability 901 Chapter 23: Cable Connectivity Issues and Tools 902 Chapter 24: Network Troubleshooting Methodology 902 Chapter 25: Network Software Tools and Commands 903 Appendix B Answers to Review Questions 905 Chapter 1: Introduction to Networks 906 Chapter 2: The Open Systems Interconnection Specifications 907 Chapter 3: Networking Connectors and Wiring Standards 909 Chapter 4: The Current Ethernet Specifications 910 Chapter 5: Networking Devices 911 Chapter 6: Introduction to the Internet Protocol 913 Chapter 7: IP Addressing 914 Chapter 8: IP Subnetting, Troubleshooting IP, and Introduction to NAT 916 Chapter 9: Introduction to IP Routing 918 Chapter 10: Routing Protocols 919 Chapter 11: Switching and Virtual LANs 921 Chapter 12: Wireless Networking 922 Chapter 13: Using Statistics and Sensors to Ensure Network Availability 924 Chapter 14: Organizational Documents and Policies 925 Chapter 15: High Availability and Disaster Recovery 926 Chapter 16: Common Security Concepts 927 Chapter 17: Common Types of Attacks 927 Chapter 18: Network Hardening Techniques 928 Chapter 19: Remote Access Security 929 Chapter 20: Physical Security 930 Chapter 21: Data Center Architecture and Cloud Concepts 931 Chapter 22: Ensuring Network Availability 933 Chapter 23: Cable Connectivity Issues and Tools 934 Chapter 24: Network Troubleshooting Methodology 935 Chapter 25: Network Software Tools and Commands 937 Appendix C Subnetting Class A 939 Subnetting Practice Examples: Class A Addresses 940 Practice Example #1A: 255.255.0.0 (/16) 941 Practice Example #2A: 255.255.240.0 (/20) 941 Practice Example #3A: 255.255.255.192 (/26) 942 Subnetting in Your Head: Class A Addresses 942 Written Lab 1 943 Written Lab 2 944 Answers to Written Lab 1 944 Answers to Written Lab 2 945 Index 947 Todd Lammle, Network+, CCSI, CCNA, CCNP, is the networking authority. He has been involved in computers and networking with Fortune 500 companies for over 30 years. Todd is President of GlobalNet System Solutions, Inc., a networking integration and training firm. He is the bestselling author of numerous titles, with over 900,000 copies of his books in print. He can be reached through his website at www.lammle.com.

Hands-on Azure Cognitive Services
Use this hands-on guide book to learn and explore cognitive APIs developed by Microsoft and provided with the Azure platform. This book gets you started working with Azure Cognitive Services. You will not only become familiar with Cognitive Services APIs for applications, but you will also be exposed to methods to make your applications intelligent for deployment in businesses.The book starts with the basic concepts of Azure Cognitive Services and takes you through its features and capabilities. You then learn how to work inside the Azure Marketplace for Bot Services, Cognitive Services, and Machine Learning. You will be shown how to build an application to analyze images and videos, and you will gain insight on natural language processing (NLP). Speech Services and Decision Services are discussed along with a preview of Anomaly Detector. You will go through Bing Search APIs and learn how to deploy and host services by using containers. And you will learn how to use Azure Machine Learning and create bots for COVID-19 safety, using Azure Bot Service.After reading this book, you will be able to work with datasets that enable applications to process various data in the form of images, videos, and text.WHAT YOU WILL LEARN* Discover the options for training and operationalizing deep learning models on Azure* Be familiar with advanced concepts in Azure ML and the Cortana Intelligence Suite architecture* Understand software development kits (SKDs)* Deploy an application to Azure Kubernetes ServiceWHO THIS BOOK IS FORDevelopers working on a range of platforms, from .NET and Windows to mobile devices, as well as data scientists who want to explore and learn more about deep learning and implement it using the Microsoft AI platformED PRICE is Senior Program Manager in Engineering at Microsoft, with an MBA degree in technology management. Previously, he led Azure Global’s efforts to publish key architectural guidance, ran Microsoft customer feedback programs for Azure Development and Data Services, and was a technical writer at Microsoft for six years, helping lead TechNet Wiki. Ed now leads Microsoft’s efforts to publish reference architectures on the Azure Architecture Center (including a strong focus on AI architectures). He is an instructor at Bellevue College, where he teaches design and computer science. At Microsoft, he also helps lead volunteer efforts to teach thousands of students how to code each year, focusing on girls and minorities. Ed is a co-author of six books, including Azure Cloud Native Architecture Mapbook, Cloud Debgging and Profiling in Microsoft Azure (Apress), and Learn to Program with Small Basic.ADNAN MASOOD, PhD, is an Artificial Intelligence and Machine Learning researcher, Software Engineer, Microsoft regional Director, and Microsoft MVP for Artificial Intelligence. An international speaker and thought leader, Adnan currently works at UST as Chief AI Architect, and collaborates with Stanford Artificial Intelligence Lab and MIT AI Lab on building enterprise solutions. Adnan has authored four books, including Automated Machine Learning and Cognitive Computing Recipes (Apress).GAURAV ARORAA is a Chief Technology officer at SCL, with Doctorate in Computer Science. Guarav is a Microsoft MVP award recipient. He is a lifetime member of the Computer Society of India (CSI), an advisory member and senior mentor at IndiaMentor, certified as a Scrum trainer and coach, ITIL-F certified, and PRINCE-F and PRINCE-P certified. Guarav is an open-source developer and a contributor to the Microsoft TechNet community. He has authored ten books, including Cloud Debugging and Profiling in Microsoft Azure (Apress).CHAPTER 1: THE POWER OF COGNITIVE SERVICESCHAPTER GOAL: This first chapter sets up the values, reasons, and impacts you can achieve through Microsoft Azure Cognitive Services. It provides an overview of the features and capabilities. The chapter also introduces you to our case study and structures that we’ll use throughout the rest of the book.NO OF PAGES: 14SUB - TOPICS1. Overview of Azure Cognitive Services2. Understanding the Use Cases3. Exploring the Cognitive Services APIs: Vision, Speech, Language, Search, and Decision4. Overview of Machine Leaning5. The COVID-19 SmartApp ScenarioCHAPTER 2: THE AZURE PORTAL FOR COGNITIVE SERVICESCHAPTER GOAL: The aim of this chapter to get started with Microsoft Cognitive services by exploring the Azure Portal. This chapter will explore the Cognitive Azure Portal and some of the common features. Finally, the chapter will take you inside the Azure Marketplace for Bot Service, Cognitive Services, and Machine Learning.NO OF PAGES: 18SUB - TOPICS1. Getting started with Azure Portal and Microsoft Cognitive Services2. Azure Marketplace – an overview of AI + Machine Learning3. Getting started with Azure Bot Service4. Understanding software development kits (SDKs) – to get started with a favorite programing language [Ref. https://docs.microsoft.com/en-us/azure/cognitive-services/]5. Setting up your Visual Studio templateCHAPTER 3: VISION – IDENTIFY AND ANALYZE IMAGES AND VIDEOSCHAPTER GOAL: This chapter will provide insight on Computer Vision with a full of hands-on example, where we build an application to analyze an Image. There are two features currently in preview that this chapter will also cover: Form Recognizer and Ink Recognizer.NO OF PAGES: 24SUB - TOPICS1. Understanding the Vision API with Computer Vision2. Analyzing images3. Identifying a face4. Understanding the working behavior of vision APIs for Video Analysis5. Recognizing forms, tables, and ink6. Summary of the Vision APICHAPTER 4: LANGUAGE – GAIN AN UNDERSTANDING OF UNSTRUCTURED TEXT AND MODELSCHAPTER GOAL: This chapter will provide insight on NLP (Natural language processing) by evaluating user sentiments. The chapter will also touch preview features – including Immersive Reader.NO OF PAGES: 20SUB - TOPICS1. Creating and understanding language models2. Training language models3. Translating text to create your own translator application4. Using QnA Maker to host conversational discussions about your data5. Using Immersive Reader to understand text via audio and visual cues6. Summary of the Language APICHAPTER 5: SPEECH – TALK TO YOUR APPLICATIONCHAPTER GOAL: This chapter will provide insight on speech services by evaluating translating text to speech and vice versa. Enabling a speaker and translating into multiple languages. The chapter will also touch a preview feature – Speaker Recognition. The Bing speech feature will not be covered as it is retiring soon.NO OF PAGES: 18SUB - TOPICS1. Understanding speech and speech services2. Converting speech into text and vice versa3. Translating speech real-time into your application4. Identifying the speaker from speech using Speaker Recognition5. Customizing speech6. Summary of the Speech APICHAPTER 6: DECISION – MAKE SMARTER DECISIONS IN YOUR APPLICATIONSCHAPTER GOAL: This chapter will provide insight on decision services by adding content a moderation facility in the application. The chapter will also touch on a preview feature – Anomaly Detector.NO OF PAGES: 17SUB - TOPICS1. Understanding the decision service and decision APIs2. Creating an auto Content Moderator application3. Creating personalized experiences with the Personalizer4. Identifying future problems with the Anomaly Detector5. Summary of the Decision APICHAPTER 7: SEARCH – ADD SEARCH CAPABILITIES TO YOUR APPLICATIONCHAPTER GOAL: This chapter will provide insight on Bing Search APIs by adding various search functionalities to the application.NO OF PAGES: 18SUB - TOPICS1. Understanding search and the Bing Search APIs2. Creating a smart application by adding Bing Search3. Suggesting a user with auto suggestions4. Summary of the Search APICHAPTER 8: DEPLOY AND HOST SERVICES USING CONTAINERSCHAPTER GOAL: This chapter will provide a complete insight on Cognitive Services containers. In this chapter, we will highlight the key feature by creating an application. The application will deploy using Docker.NO OF PAGES: 22SUB - TOPICS1. Getting started with Cognitive Services containers2. Understanding deployment and how to deploy and run a container on an Azure container instance3. Understand Docker compose and use it to deploy multiple containers4. Understanding Azure Kubernetes Service and how to deploy an application to Azure Kubernetes ServiceCHAPTER 9: AZURE BOT SERVICECHAPTER GOAL: This chapter will provide insight on Bot Service by creating the COVID-19 Bot.NO OF PAGES: 24SUB - TOPICS1. Understanding Azure Bot services2. Create a COVID-19 Bot using Azure Bot Service3. Using the Azure Bot Builder SDK. Reference: https://docs.microsoft.com/en-us/azure/bot-service/dotnet/bot-builder-dotnet-sdk-quickstart?view=azure-bot-service-4.0CHAPTER 10: AZURE MACHINE LEARNINGCHAPTER GOAL: This chapter will lead the reader to fully understand Azure Machine Learning and how to use it. You can train your application to learn without being explicitly programmed. We will include forecasts and predictions. The chapter will cover a preview feature – Azure Machine Learning designer.NO OF PAGES: 22SUB - TOPICS1. Building models with no-code, using the Azure Machine Learning designer2. Publishing to Jupyter notebooks3. Building ML models in Python or R4. The ML Visual Studio Code extension5. Commanding the ML CLI6. Summary of ML

MERN Projects for Beginners
Learn how to use the MERN stack (MongoDB, Express.js, React, and Node) to build five fully functioning web apps for dating, video sharing, messaging, and social media. While creating these web apps, you’ll learn key development concepts including how to use React hooks, Redux, MongoDB, Express, Heroku, Firebase, Material UI, and Google authentication. By expanding your portfolio with the projects you create, you will be well equipped as front-end developer.You will first create a dating site with a swiping feature and chat functionality. You will then build a video sharing app with videos displaying vertically. Next, you will learn to build an awesome messaging web app. Users will be able to chat in real time, as well as log in to their account using Google authentication. You will also create a photo sharing app and social media web apps with the ability to post images with captions and log in using email and password authentication.Most MERN tutorials out there today cover basic web apps but it is capable of so much more – learn how to use this stack to its full potential and build projects that can be converted into full scaled start-ups with additional features.WHAT YOU'LL LEARN* Work with React hooks and React router* Examine powerful MongoDB services for easy to use and setup* Create routes using Node and host on Heroku* Study different authentication techniques* Deploy all sites using simple Firebase hosting* Use the powerful React ecosystem to add functionalities to your appsWHO THIS BOOK IS FORThose who have just started their career in web development and have basic knowledge of the core web technologies: HTML, CSS, and JavaScript. Those with basic React development and feel ready to explore its capabilities further.NABENDU BISWAS is a full stack JavaScript developer who has been working in the IT industry for the past 16 years and has worked for some of the world’s top development firms and investment banks. He is a passionate tech blogger who publishes on dev.to and medium.com and on thewebdev.tech. He is an all-round nerd, passionate about everything JavaScript, React and Gatsby. You can find him on Twitter @nabendu82.Chapter One: Setting Up Our EnvironmentChapter Two: Dating App· Firebase hosting initial setup· React basic setup· Adding Swipe functionality· Setting up MongoDB database· Creating NodeJS schema and routes· Integrating backend with React· Deploying backend in heroku· Hosting through firebaseChapter Three : Video Sharing App· Firebase hosting initial setup· React basic setup· Adding Short videos to site· Adding snap feature to video· Setting up MongoDB database· Creating NodeJS schema and routes· Integrating backend with React· Deploying backend in heroku· Hosting through firebaseChapter Four: Messaging App· Firebase hosting initial setup· React basic setup· Creating Sidebar component showing rooms· Creating the Chat functionality· Setting up MongoDB database· Creating NodeJS schema and routes· Adding real-time chat with Pusher· Integrating backend with React· Adding Google authentication· Deploying backend in heroku· Hosting through firebaseChapter Five: Photo-based Social Network· Firebase hosting initial setup· React basic setup· Showing images with caption on site· Setting up MongoDB database· Creating NodeJS schema and routes· Adding real-time posts with Pusher· Integrating backend with React· Adding email/password authentication· Adding Signup and Sign-in to site· Adding ability to add post· Adding ability to comment on post· Deploying backend in heroku· Hosting through firebaseChapter Six: More Complex Social Network· Firebase hosting initial setup· React basic setup and adding styled components· Showing basic structure of the site· Adding Google authentication· Setting up MongoDB database· Creating NodeJS schema and routes· Adding file upload with Multer· Integrating backend with React· Adding ability to add post· Adding real-time posts with Pusher· Deploying backend in heroku· Hosting through firebase

IoT Standards with Blockchain
Implement a standardized end-to-end IoT implementation based on best practices and proven successes in IoT across multiple industries. With this book you'll discover the three business strategies for enterprises to adopt and remain relevant in the marketspace —the Customer Engagement strategy, the Business Transformation strategy, and the Business Productivity Improvement strategy. Pick the right strategy for your enterprise to ensure a clear mission and vision is established based on which IoT roadmap can be defined. Subsequently all business processes pertaining to the chosen business strategy are investigated to define use cases where IoT can be adopted to achieve that business strategy.Start by learning the generic industry perspective on digital transformation using IoT. Then move on to the IoT Standards Reference Model. It’s an abstract framework consisting of an interlinked set of clearly defined components for enterprises to successfully implement an IoT solution. The IoT Standards Reference Model can be applied for IoT use cases across any industry and is kept abstract in order to enable many, potentially different, IoT architectures to be implemented based on the model.With IoT thoroughly covered, you’ll dive into Blockchain and AI technology. This book will discuss the importance of using private blockchains for IoT use cases. You’ll also discover the five IoT-Blockchain implementation patterns that enterprises can enable for seamless communication between IoT devices, IoT Smart Gateways, and IoT platforms. These patterns help achieve trust, interoperability, and extendibility. Then you’ll work with AI and the IoT Standards Reference Model. The reference model recommends applying AI patterns to generate insights from data and take appropriate actions automatically.IoT Standards with Blockchain also provides perspective on how and when to apply AI in an IoT Context. In the end, you’ll have a solid methodology to execute large scale, enterprise-level IoT implementations. You’ll have an enterprise digital transformation framework for IoT that will enable your enterprise to operate better.WHAT YOU'LL LEARN* Facilitate IoT interoperability with best practices* Implement IoT platform security* Feed data and analytics to AI modelsWHO THIS BOOK IS FORC-suite leaders and IT program managers across all industries, including manufacturing (Industry 4.0), logistics, oil and gas, transportation, energy, mining and metals, aviation, pharmaceuticals, medical devices, and hospitality. VENKATESH UPADRISTA leads UKI delivery for HCL Technologies—an 8 Billion Solutions IT Services company. He is recognized as an exceptional digital talent leader by UK Tech Nation and speaks at industry conferences on topics covering the Internet of Things and other digital focuses.Part 1: IoT Business StrategyChapter 1: Getting StartedDesigning Business for FutureThe Triple Challenges in IoTChapter 2: IoT Business StrategyCustomer Engagement StrategyBusiness Transformation StrategyBusiness Productivity ImprovementChoosing Between Customer Engagement, Business Transformation, and Business Productivity Improvement StrategyChapter 3: IoT Standards Business Transformation ModelWhat next after your business strategy is chosenThe IoT Use Case Reference Model (IoT UCR ModeL)Applying IoT Treatments on Use CasesPart II: The IoT Reference ModelChapter 4: The IoT Reference ModelTh IoT Standards Reference ModelFullStack IoT PlatformTypical activities performed by Smart IoT gateway and Full Stack IoT PlatformSecurityBlockchainChapter 5: IoT Device and Their CommunicationDevice TypesCommunication ProtocolsChapter 6: The Smart IoT GatewayData Volume and AnalyticsIoT GatewaysSmart IoT GatewaysChoosing the right Smart IoT gatewayIoT gateway ComparisonsChapter 7: IoT Cloud PlatformIoT Basics SixSpecific CapabilitiesProof-of-Concept (PoC)Chapter 8: Security in IoTSecure by DESIGN (Securing the whole IoT ecosystem)Securing IoT Using BlockchainPart III: AI and Blockchain as Enablers for IoTChapter 9: Blockchain with IoTPublic BlockchainPrivate BlockchainIoT Blockchain implementation PatternsChapter 10: Artificial Intelligence in the IoT World (Applied IoT)Robotic process automationArtificial IntelligenceArtificial Intelligence & IoTLessons learned in applying AI in IoT Use Cases (Applied IoT)Part IV: IoT Implementation AspectsChapter 11: Big Data and AnalyticsDebugging Capabilities(Big) Data First Reference ModelChapter 12: Product Mindset for IoT Use Case ImplementationProduct OrganizationIoT Product Lifecycle with Product MindsetChapter 13: IoT Product TeamIoT Product TeamIoT Product Team IdentificationAudience: Intermediate

The Self-Taught Computer Scientist
THE FOLLOW-UP TO CORY ALTHOFF'S BESTSELLING THE SELF-TAUGHT PROGRAMMER, WHICH INSPIRED HUNDREDS OF THOUSANDS OF PROFESSIONALS TO LEARN TO PROGRAM OUTSIDE OF SCHOOL!Fresh out of college and with just a year of self-study behind him, Cory Althoff was offered a dream first job as a software engineer for a well-known tech company, but he quickly found himself overwhelmed by the amount of things he needed to know, but hadn’t learned yet. This experience combined with his personal journey learning to program inspired his widely praised guide, The Self-Taught Programmer. Now Cory's back with another guide for the self-taught community of learners focusing on the foundations of computer science.The Self-Taught Computer Scientist introduces beginner and self-taught programmers to computer science fundamentals that are essential for success in programming and software engineering fields. Computer science is a massive subject that could cover an entire lifetime of learning. This book does not aim to cover everything you would learn about if you went to school to get a computer science degree. Instead, Cory's goal is to give you an introduction to some of the most important concepts in computer science that apply to a programming career. With a focus on data structures and algorithms, The Self-Taught Computer Scientist helps you fill gaps in your knowledge, prepare for a technical interview, feel knowledgeable and confident on the job, and ultimately, become a better programmer.* Learn different algorithms including linear and binary search and test your knowledge with feedback loops* Understand what a data structure is and study arrays, linked lists, stacks, queues, hash tables, binary trees, binary heaps, and graphs* Prepare for technical interviews and feel comfortable working with more experienced colleagues* Discover additional resources and tools to expand your skillset and continue your learning journeyIt's as simple as this: You have to study computer science if you want to become a successful programmer, and if you don't understand computer science, you won't get hired. Ready for a career in programming, coding, or software engineering and willing to embrace an "always be learning" mindset? The Self-Taught Computer Scientist is for you.CORY ALTHOFF is a programmer, speaker, and author whose work includes The Self-Taught Programmer and The Self-Taught Computer Scientist. After graduating with a major in political science, Cory taught himself to program, eventually becoming a software engineer at eBay. Cory's books have been translated into eight languages, and he has been featured in publications like Forbes and CNBC. Over 250K developers are part of the self-taught programmer community he created through his popular Facebook group, course, and newsletter. Cory is a senior vice president at CompTIA, where he helps people learn the skills they need to have successful careers in tech. Cory lives in California with his wife and daughter.Introduction xivI INTRODUCTION TO ALGORITHMS 11 WHAT IS AN ALGORITHM? 3Analyzing Algorithms 4Constant Time 8Logarithmic Time 9Linear Time 10Log-Linear Time 11Quadratic Time 11Cubic Time 13Exponential Time 14Best-Case vs. Worst-Case Complexity 15Space Complexity 15Why is This Important? 16Vocabulary 17Challenge 182 RECURSION 19When to Use Recursion 23Vocabulary 23Challenge 233 SEARCH ALGORITHMS 25Linear Search 25When to Use a Linear Search 27Binary Search 27When to Use a Binary Search 30Searching for Characters 32Vocabulary 34Challenge 354 SORTING ALGORITHMS 37Bubble Sort 37When to Use Bubble Sort 41Insertion Sort 42When to Use Insertion Sort 45Merge Sort 45When to Use Merge Sort 52Sorting Algorithms in Python 53Vocabulary 54Challenge 545 STRING ALGORITHMS 55Anagram Detection 55Palindrome Detection 56Last Digit 57Caesar Cipher 58Vocabulary 61Challenge 616 MATH 63Binary 63Bitwise Operators 66FizzBuzz 70Greatest Common Factor 72Euclid’s Algorithm 74Primes 75Vocabulary 77Challenge 787 SELF-TAUGHT INSPIRATION: MARGARET HAMILTON 79II DATA STRUCTURES 818 WHAT IS A DATA STRUCTURE? 83Vocabulary 85Challenge 869 ARRAYS 87Array Performance 88Creating an Array 90Moving Zeros 91Combining Two Lists 94Finding the Duplicates in a List 95Finding the Intersection of Two Lists 98Vocabulary 99Challenge 10010 LINKED LISTS 101Linked List Performance 103Create a Linked List 104Search a Linked List 107Removing a Node from a Linked List 108Reverse a Linked List 109Finding a Linked List Cycle 110Vocabulary 111Challenges 11211 STACKS 113When to Use Stacks 114Creating a Stack 115Using Stacks to Reverse Strings 119Min Stack 120Stacked Parentheses 123Vocabulary 125Challenges 12512 QUEUES 127When to Use Queues 128Creating a Queue 129Python’s Built-In Queue Class 134Create a Queue Using Two Stacks 134Vocabulary 136Challenge 13613 HASH TABLES 137When to Use Hash Tables 140Characters in a String 141Two Sum 143Vocabulary 144Challenge 14514 BINARY TREES 147When to Use Trees 150Creating a Binary Tree 153Breadth-First Tree Traversal 155More Tree Traversals 157Invert a Binary Tree 160Vocabulary 162Challenges 16215 BINARY HEAPS 163When to Use Heaps 167Creating a Heap 167Connecting Ropes with Minimal Cost 169Vocabulary 171Challenge 17116 GRAPHS 173When to Use Graphs 177Creating a Graph 178Dijkstra’s Algorithm 180Vocabulary 186Challenge 18717 SELF-TAUGHT INSPIRATION: ELON MUSK 18918 NEXT STEPS 191What’s Next? 191Climbing the Freelance Ladder 192How to Get an Interview 192How to Prepare for a Technical Interview 193Additional Resources 194Final Thoughts 194Index 195

Developer Relations
Increasingly, business leaders are either looking to start a new developer program at their company or looking to increase the impact of their existing DevRel program. In this context, software developers are finally recognized as legitimate decision makers in the technology buying process, regardless of the size of their organization. New companies are appearing with the sole purpose of making tools for developers, and even companies whose primary focus was elsewhere are waking up to the developer opportunity. Even as the need and demand for DevRel has grown, there are still re-occurring challenges for DevRel leaders.It is these challenges that this book addresses, covering all aspects of a DevRel program. It is an essential reference to professionalize the practice of developer relations by providing you with strategic, repeatable, and adoptable frameworks, processes, and tools, including developer segmentation and personas, and developer experience frameworks.InDeveloper Relations, you’ll find the answers to the following questions:* How do we convince stakeholders to support a program?* How do we go about creating a program?* How do we make developers aware of our offer?* How do we stand out from the crowd?* How do we get developers to use our products?* How do we ensure developers are successful using our products?* How do we measure success?* How do we maintain the support of our stakeholders?After reading this book you’ll have a clear definition of what developer relations is, the type of companies that engage in DevRel, and the scope and business models involved.WHAT YOU WILL LEARN* Discover what developer relations is and how it contributes to a company’s success* Launch a DevRel program * Operate a successful program * Measure the success of your program* Manage stakeholders WHO THIS BOOK IS FORThose interested in starting a new developer program or looking to increase the impact of their existing one. From executives to investors, from marketing professionals to engineers, all will find this book useful to realize the impact of developer relations.PART 1: DEVELOPING A COMMON UNDERSTANDING.- 1. What is Developer Relations?.- 2. Where does Developer Relations Fit?- 3. The Origin of Developer Relations & The Rise of the Developer.- 4. The Value of the Developer Economy.- PART 2: THE KEY DIFFERENTIATORS OF DEVELOPER RELATIONS.- 5. The Audience: Developers.- 6. Developers as Decision Makers.- 7. Developer First & Dev Plus.- 8.Business Models.- 9. Developer Products.- PART 3: ALIGNMENT ON GOALS.- 10. Corporate Alignment.- 11. Program Goals.- PART 4: GO TO MARKET/STRATEGY ACTIVATION.- 12. Developer Segmentation.- 13. Developer Personas.- 14. Developer Messaging.- 15. The Developer Journey.- 16. Discover.- 17. Developer Experience.- 18. Evaluate.- 19. Learn.- 20. Build.- 21. Scale.- 22. Communities.-PART 5: MEASURE.- 23. Metrics.- PART 6: GROWING YOUR PROGRAM.- 24. Team.- 25. Program Maturity.- 26. What Comes Next?.- Appendix.

Information Security
PROVIDES SYSTEMATIC GUIDANCE ON MEETING THE INFORMATION SECURITY CHALLENGES OF THE 21ST CENTURY, FEATURING NEWLY REVISED MATERIAL THROUGHOUTInformation Security: Principles and Practice is the must-have book for students, instructors, and early-stage professionals alike. Author Mark Stamp provides clear, accessible, and accurate information on the four critical components of information security: cryptography, access control, security protocols, and software. Readers are provided with a wealth of real-world examples that clarify complex topics, highlight important security issues, and demonstrate effective methods and strategies for protecting the confidentiality and integrity of data.Fully revised and updated, the third edition of Information Security features a brand-new chapter on network security basics and expanded coverage of cross-site scripting (XSS) attacks, Stuxnet and other malware, the SSH protocol, secure software development, and security protocols. Fresh examples illustrate the Rivest-Shamir-Adleman (RSA) cryptosystem, Elliptic-curve cryptography (ECC), and hash functions based on bitcoin and blockchains. Updated problem sets, figures, tables, and graphs help readers develop a working knowledge of classic cryptosystems, symmetric and public key cryptography, cryptanalysis, simple authentication protocols, intrusion and malware detection systems, and more. Presenting a highly practical approach to information security, this popular textbook:* Provides up-to-date coverage of the rapidly evolving field of information security* Explains session keys, perfect forward secrecy, timestamps, SSH, SSL, IPSec, Kerberos, WEP, GSM, and other authentication protocols* Addresses access control techniques including authentication and authorization, ACLs and capabilities, and multilevel security and compartments* Discusses software tools used for malware detection, digital rights management, and operating systems security* Includes an instructor’s solution manual, PowerPoint slides, lecture videos, and additional teaching resourcesInformation Security: Principles and Practice, Third Edition is the perfect textbook for advanced undergraduate and graduate students in all Computer Science programs, and remains essential reading for professionals working in industrial or government security.To request supplementary materials, please contact mark.stamp@sjsu.edu and visit the author-maintained website for more: https://www.cs.sjsu.edu/~stamp/infosec/ [https://urldefense.com/v3/__https:/www.cs.sjsu.edu/*stamp/infosec/__;fg!!N11eV2iwtfs!vQiT_RPMbK65YTVJVaaG1i4R6paBRZB91H3juc9ejhGB1vRRIH-7YPUI7_GjtuXF_7mJyM39sfFjrtfZOkSIbw$] .MARK STAMP, PHD, has more than 25 years of experience in the field of information security. He has worked in industry, in academia as Professor of Computer Science, and in government as a cryptologic scientist for the National Security Agency. He has written dozens of academic papers, numerous journal articles, and two books on the topic of information security. Preface xvAbout The Author xixAcknowledgments xxi1 Introductions 11.1 The Cast of Characters 11.2 Alice's Online Bank 21.2.1 Confidentiality, Integrity, and Availability 21.2.2 Beyond CIA 21.3 About This Book 41.3.1 Cryptography 41.3.2 Access Control 51.3.3 Network Security 61.3.4 Software 61.4 The People Problem 71.5 Principles and Practice 71.6 Problems 8I Crypto 132 Classic Cryptography 152.1 Introduction 152.2 How to Speak Crypto 152.3 Classic Crypto 172.3.1 Simple Substitution Cipher 182.3.2 Cryptanalysis of a Simple Substitution 202.3.3 Definition of Secure 212.3.4 Double Transposition Cipher 222.3.5 One-Time Pad 232.3.6 Codebook Cipher 27viii CONTENTS2.4 Classic Crypto in History 282.4.1 Ciphers of the Election of 1876 282.4.2 Zimmermann Telegram 302.4.3 Project VENONA 322.5 Modern Crypto History 332.6 A Taxonomy of Cryptography 362.7 A Taxonomy of Cryptanalysis 372.8 Summary 392.9 Problems 393 Symmetric Ciphers 453.1 Introduction 453.2 Stream Ciphers 463.2.1 A5/1 473.2.2 RC4 493.3 Block Ciphers 513.3.1 Feistel Cipher 513.3.2 DES 523.3.3 Triple DES 573.3.4 AES 593.3.5 TEA 623.3.6 Block Cipher Modes 643.4 Integrity 683.5 Quantum Computers and Symmetric Crypto 703.6 Summary 723.7 Problems 724 Public Key Crypto 794.1 Introduction 794.2 Knapsack 824.3 RSA 854.3.1 Textbook RSA Example 874.3.2 Repeated Squaring 884.3.3 Speeding Up RSA 904.4 Diffie-Hellman 914.5 Elliptic Curve Cryptography 934.5.1 Elliptic Curve Math 934.5.2 ECC Diffie-Hellman 954.5.3 Realistic Elliptic Curve Example 964.6 Public Key Notation 974.7 Uses for Public Key Crypto 984.7.1 Confidentiality in the Real World 984.7.2 Signatures and Non-repudiation 99CONTENTS ix4.7.3 Confidentiality and Non-repudiation 994.8 Certificates and PKI 1024.9 Quantum Computers and Public Key 1044.10 Summary 1064.11 Problems 1065 Crypto Hash Functions++ 1155.1 Introduction 1155.2 What is a Cryptographic Hash Function? 1165.3 The Birthday Problem 1175.4 A Birthday Attack 1195.5 Non-Cryptographic Hashes 1205.6 SHA-3 1215.7 HMAC 1245.8 Cryptographic Hash Applications 1265.8.1 Online Bids 1265.8.2 Blockchain 1275.9 Miscellaneous Crypto-Related Topics 1365.9.1 Secret Sharing 1365.9.2 Random Numbers 1405.9.3 Information Hiding 1435.10 Summary 1475.11 Problems 147II Access Control 1596 Authentication 1616.1 Introduction 1616.2 Authentication Methods 1626.3 Passwords 1636.3.1 Keys Versus Passwords 1646.3.2 Choosing Passwords 1646.3.3 Attacking Systems via Passwords 1666.3.4 Password Verification 1676.3.5 Math of Password Cracking 1686.3.6 Other Password Issues 1736.4 Biometrics 1746.4.1 Types of Errors 1766.4.2 Biometric Examples 1766.4.3 Biometric Error Rates 1816.4.4 Biometric Conclusions 1826.5 Something You Have 182x CONTENTS6.6 Two-Factor Authentication 1836.7 Single Sign-On and Web Cookies 1836.8 Summary 1846.9 Problems 1857 Authorization 1957.1 Introduction 1957.2 A Brief History of Authorization 1967.2.1 The Orange Book 1967.2.2 The Common Criteria 1997.3 Access Control Matrix 2007.3.1 ACLs and Capabilities 2017.3.2 Confused Deputy 2027.4 Multilevel Security Models 2047.4.1 Bell-LaPadula 2067.4.2 Biba's Model 2077.4.3 Compartments 2087.5 Covert Channels 2107.6 Inference Control 2127.7 CAPTCHA 2147.8 Summary 2167.9 Problems 216III Topics in Network Security 2218 Network Security Basics 2238.1 Introduction 2238.2 Networking Basics 2238.2.1 The Protocol Stack 2258.2.2 Application Layer 2268.2.3 Transport Layer 2288.2.4 Network Layer 2318.2.5 Link Layer 2338.3 Cross-Site Scripting Attacks 2358.4 Firewalls 2368.4.1 Packet Filter 2388.4.2 Stateful Packet Filter 2408.4.3 Application Proxy 2408.4.4 Defense in Depth 2428.5 Intrusion Detection Systems 2438.5.1 Signature-Based IDS 2458.5.2 Anomaly-Based IDS 246CONTENTS xi8.6 Summary 2508.7 Problems 2509 Simple Authentication Protocols 2579.1 Introduction 2579.2 Simple Security Protocols 2599.3 Authentication Protocols 2619.3.1 Authentication Using Symmetric Keys 2649.3.2 Authentication Using Public Keys 2679.3.3 Session Keys 2689.3.4 Perfect Forward Secrecy 2709.3.5 Mutual Authentication, Session Key, and PFS 2739.3.6 Timestamps 2739.4 ``Authentication"" and TCP 2759.5 Zero Knowledge Proofs 2789.6 Tips for Analyzing Protocols 2829.7 Summary 2849.8 Problems 28410 Real-World Security Protocols 29310.1 Introduction 29310.2 SSH 29410.2.1 SSH and the Man-in-the-Middle 29510.3 SSL 29610.3.1 SSL and the Man-in-the-Middle 29910.3.2 SSL Connections 30010.3.3 SSL Versus IPsec 30010.4 IPsec 30110.4.1 IKE Phase 1 30210.4.2 IKE Phase 2 30910.4.3 IPsec and IP Datagrams 31010.4.4 Transport and Tunnel Modes 31110.4.5 ESP and AH 31310.5 Kerberos 31410.5.1 Kerberized Login 31610.5.2 Kerberos Ticket 31610.5.3 Security of Kerberos 31810.6 WEP 31910.6.1 WEP Authentication 31910.6.2 WEP Encryption 32010.6.3 WEP Non-Integrity 32010.6.4 Other WEP Issues 32110.6.5 WEP: The Bottom Line 322xii CONTENTS10.7 GSM 32210.7.1 GSM Architecture 32310.7.2 GSM Security Architecture 32410.7.3 GSM Authentication Protocol 32610.7.4 GSM Security Flaws 32710.7.5 GSM Conclusions 32910.7.6 3GPP 33010.8 Summary 33010.9 Problems 331IV Software 33911 Software Flaws and Malware 34111.1 Introduction 34111.2 Software Flaws 34111.2.1 Buffer Overflow 34511.2.2 Incomplete Mediation 35611.2.3 Race Conditions 35611.3 Malware 35811.3.1 Malware Examples 35911.3.2 Malware Detection 36511.3.3 The Future of Malware 36711.3.4 The Future of Malware Detection 36911.4 Miscellaneous Software-Based Attacks 36911.4.1 Salami Attacks 36911.4.2 Linearization Attacks 37011.4.3 Time Bombs 37111.4.4 Trusting Software 37211.5 Summary 37311.6 Problems 37312 Insecurity in Software 38112.1 Introduction 38112.2 Software Reverse Engineering 38212.2.1 Reversing Java Bytecode 38412.2.2 SRE Example 38512.2.3 Anti-Disassembly Techniques 39012.2.4 Anti-Debugging Techniques 39112.2.5 Software Tamper Resistance 39212.3 Software Development 39312.3.1 Flaws and Testing 39512.3.2 Secure Software Development? 396CONTENTS xiii12.4 Summary 39612.5 Problems 397Appendix 403A-1 Modular Arithmetic 403A-2 Permutations 405A-3 Probability 406A-4 DES Permutations 406Index 418

Performance Testing
Use this book to prepare for the ISTQB® Certified Tester Foundation Level Performance Testing exam. The book has been designed to follow the ISTQB syllabus, covering all of the syllabus learning objectives, with additional reference material extending beyond the syllabus. The book covers an overall methodology for managing and conducting performance testing.Performance testing has often been considered a black art. In many organizations, perhaps an individual or a small group of technical staff or contractors is given the task of “load testing” an extended system, network, or application.Performance testing is like any other form of testing. It follows a defined test process that is similar to other test types. It utilizes a disciplined approach to the definition of requirements and user stories, the creation of test conditions, test cases, and test procedures. It establishes measurable goals against which the success or failure of the testing can be judged. It also requires (and this cannot be stressed highly enough) a definition and recognition of performance test failures.Readers will gain the knowledge with both content and practice questions to prepare them for the ISQTB Performance Testing exam. The book covers the performance test types, the performance testing methodology, and the steps to plan, create, and execute performance tests and analyze the results.WHAT YOU WILL LEARN* Understand the basic concepts of performance efficiency and performance testing* Define performance risks, goals, and requirements to meet stakeholder needs and expectations* Understand performance metrics and how to collect them* Develop a performance test plan for achieving stated goals and requirements* Conceptually design, implement, and execute basic performance tests* Analyze the results of a performance test and communicate the implications to stakeholders* Explain the process, rationale, results, and implications of performance testing to stakeholders* Understand the categories and uses for performance tools and criteria for their selection* Determine how performance testing activities align with the software life cycleWHO THIS BOOK IS FORThose who want to achieve the ISTQB performance testing certification, testers and test managers who want to increase their performance testing knowledge, and project managers/staff working with performance testing in their project for the first timeAfter a circuitous route into IT, KEITH YORKSTON has spent the last 20 years involved with software quality and risk. Cutting his teeth early in performance testing before good books were written on the subject, Keith went on to work as a consultant and trainer across the world. He currently works as an independent consultant specializing in performance and security.IntroductionChapter 1. The Basic Concepts of Performance TestingISTQB® KeywordsOther Keywords1.1 Principles of Performance Testing1.2 Types of Performance TestingPerformance TestingLoad TestingStress TestingScalability TestingSpike TestingEndurance TestingConcurrency TestingCapacity Testing1.3 Testing Activities in Performance TestingStatic TestingDynamic Testing1.4 The Concept of Load GenerationLoad Generation via the User InterfaceLoad Generation Using CrowdsLoad Generation via the Application Programming Interface (API)Load Generation using Captured Communication Protocols1.5 Common Performance Efficiency Failure Modes and Their CausesChapter 1 QuestionsChapter 2. Performance Measurement FundamentalsISTQB® KeywordsOther Keywords2.1 Typical Measurements Collected in Performance TestingWhy Performance Metrics Are NeededCollecting Performance Measurements and MetricsSelecting Performance Metrics2.2 Aggregating Results from Performance Testing2.3 Key Sources of Performance Metrics2.4 Typical Results of a Performance TestChapter 2 QuestionsChapter 3. Performance Testing in the Software LifecycleISTQB® Keywords3.1 Principal Performance Testing Activities3.2 Categories of Performance Risks for Different ArchitecturesSingle Computer SystemsMulti-tier SystemsDistributed SystemsVirtualised SystemsDynamic/Cloud-based SystemsClient –Server SystemsMobile ApplicationsEmbedded Real-time SystemsMainframe Applications3.3 Performance Risks Across the Software Development Lifecycle3.4 Performance Testing ActivitiesSequential Development ModelsIterative and Incremental Development ModelsCommercial Off-the-Shelf (COTS) and other Supplier/Acquirer ModelsChapter 3 QuestionsChapter 4. Performance Testing TasksISTQB® Keywords4.1 Planning4.1.1 Deriving Performance Test Objectives4.1.2 The Performance Test Plan4.1.3 Communicating about Performance Testing4.2 Analysis, Design and Implementation4.2.1 Typical Communication Protocols4.2.2 Transactions4.2.3 Identifying Operational Profiles4.2.4 Creating Load Profiles4.2.5 Analysing Throughput and Concurrency4.2.6 Basic Structure of a Performance Test Script4.2.7 Implementing Performance Test Scripts4.2.8 Preparing for Performance Test Execution4.3 Execution4.4 Analysing Results and ReportingAnalysis TechniquesReportingChapter 4 QuestionsChapter 5. ToolsISTQB® Keywords5.1 Tool Support5.2 Tool SuitabilityChapter 5 QuestionsChapter 6. References6.1 Standards6.2 ISTQB® Documents6.3 Books6.4 Papers and ArticlesChapter 7. Question Answers7.1 Chapter 17.2 Chapter 2

Artificial intelligence and the future of warfare
This volume offers an innovative and counter-intuitive study of how and why artificial intelligence-infused weapon systems will affect the strategic stability between nuclear-armed states. Johnson demystifies the hype surrounding artificial intelligence (AI) in the context of nuclear weapons and, more broadly, future warfare. The book highlights the potential, multifaceted intersections of this and other disruptive technology – robotics and autonomy, cyber, drone swarming, big data analytics, and quantum communications – with nuclear stability. Anticipating and preparing for the consequences of the AI-empowered weapon systems are fast becoming a critical task for national security and statecraft. Johnson considers the impact of these trends on deterrence, military escalation, and strategic stability between nuclear-armed states – especially China and the United States. The book draws on a wealth of political and cognitive science, strategic studies, and technical analysis to shed light on the coalescence of developments in AI and other disruptive emerging technologies. Artificial intelligence and the future of warfare sketches a clear picture of the potential impact of AI on the digitized battlefield and broadens our understanding of critical questions for international affairs. AI will profoundly change how wars are fought, and how decision-makers think about nuclear deterrence, escalation management, and strategic stability – but not for the reasons you might think. James Johnson is an Assistant Professor in the School of Law and Government at Dublin City University Introduction: Opening the AI Pandora’s box Part I: Destabilizing AI renaissance 1 Military AI primer 2 Artificial intelligence in the 2nd nuclear age Part II: Military AI superpowers 3 New challenges to military-techno Pax Americana 4 U.S.-China crisis stability under the AI nuclear shadow Part III: Nuclear instability redux? 5 Hunting for nuclear weapons in the digital age 6 Fast and the furious: Drone swarming and hypersonic weapons 7 The AI-cyber security nexus 8 Delegating strategic decisions to intelligent machines Conclusion: Managing an AI future Index

Cryptography and Cryptanalysis in MATLAB
Master the essentials of cryptography and cryptanalysis and learn how to put them to practical use. Each chapter of this book starts with an introduction to the concepts on which cryptographic algorithms are based and how they are used in practice, providing fully working examples for each of the algorithms presented. Implementation sections will guide you through the entire process of writing your own applications and programs using MATLAB.Cryptography and Cryptanalysis in MATLAB will serve as your definitive go-to cryptography reference, whether you are a student, professional developer, or researcher, showing how a multitude of cryptographic challenges can be overcome using the powerful tools of MATLAB.WHAT YOU WILL LEARN* Discover MATLAB’s cryptography functions* Work with conversion mechanisms in MATLABImplement cryptographic algorithms using arithmetic operations * Understand the classical, simple cryptosystems that form the basis of modern cryptography* Develop fully working solutions (encryption/decryption operations)* Study pseudo-random generators and their real-life implementations* Utilize hash functions by way of practical examples* Implement solutions to defend against practical cryptanalysis methods and attacks* Understand asymmetric and symmetric encryption systems and how to use themLeverage visual cryptography, steganography, and chaos-based cryptographyWHO THIS BOOK IS FORThose who are new to cryptography/analysis. Some prior exposure to MATLAB recommended.MARIUS IULIAN MIHAILESCU, PHD is CEO at Dapyx Solution Ltd., a company based in Bucharest, Romania and involved in information security- and cryptography-related research projects. He is a lead guest editor for applied cryptography journals and a reviewer for multiple publications with information security and cryptography profiles. He authored and co-authored more than 30 articles in conference proceedings, 25 articles in journals, and three books. For more than six years he has served as a lecturer at well-known national and international universities (University of Bucharest, “Titu Maiorescu” University, Kadir Has University in, Istanbul, Turkey). He has taught courses on programming languages (C#, Java, C++, Haskell), and object-oriented system analysis and design with UML, graphs, databases, cryptography and information security. He served for three years as IT Officer at Royal Caribbean Cruises Ltd. where he dealt with IT infrastructures, data security, and satellite communications systems. He received his PhD in 2014 and his thesis was on applied cryptography over biometrics data. He holds two MSc in information security and software engineering.STEFANIA LOREDANA NITA, PHD is a software developer at the Institute of Computer Science of the Romanian Academy and a Fellow PhD with her thesis on advanced cryptographic schemes using searchable encryption and homomorphic encryption. She has served more than two years as an assistant lecturer at the University of Bucharest where she taught courses on subjects such as advanced programming techniques, simulation methods, and operating systems. She has authored and co-authored more than 15 workpapers at conferences and journals, and has authored two books on he Haskell programming language. She is a lead guest editor for special issues on information security and cryptography such as Advanced Cryptography and Its Future: Searchable and Homomorphic Encryption. She holds an MSc in software engineering and two BSc in computer science and mathematics.NEW ToCChapter 01 – IntroductionChapter 02 – MATLAB Cryptography FunctionsChapter 03 – Conversions used in CryptographyChapter 04 – Basic Arithmetic FoundationsChapter 05 – Number TheoryChapter 06 – Classical Cryptography6.1. Caesar Cipher6.2. VigenereChapter 07 – Pseudo Random GeneratorsChapter 08 – Hash FunctionsChapter 09 – Formal Techniques for CryptographyChapter 10 – Symmetric Encryption Schemes10.1. Case Study: The Data Encryption Standard (DES)10.2. Advanced Encryption Standard (AES)Chapter 11 – Asymmetric Encryption Schemes11.1. RSA11.2. El Gamal11.3. Knapsack11.4. Merkle-HellmanChapter 12 – Visual CryptographyChapter 13 – SteganographyChapter 14 – Chaos-based CryptographyPART 1 - FOUNDATIONS.1. Cryptography Fundamentals2. Mathematical Background and Its Applicability3. Large Integer Arithmetic4. Floating-point Arithmetic5. New Features in MATLAB 106. Secure Coding Guidelines7. Cryptography Libraries in MATLABPART 2 – PRO CRYPTOGRAPHY.8. Elliptic-curve Cryptography and Public Key Algorithms9. Lattice-based Cryptography10. Searchable Encryption11. Homomorphic Encryption12. Learning with Errors and Ring Learning with Errors Cryptography13. Chaos-based Cryptography14. Big Data Cryptography15. Cloud Computing Cryptography.PART 3 – PRO CRYPTANALYSIS16. Introduction to Cryptanalysis17. General notions for Conducting Cryptanalysis Attacks18. Linear and Differential Cryptanalysis19. Integral Cryptanalysis20. Attacks21. Text Characterization22. Basic Implementations of Cryptanalysis Methods.

Semantische Datenintelligenz im Einsatz
Semantische Technologien haben mit der Entwicklung von datenbasierten Systemen wie Neuronale Netze, Deep Learning und Machine Learning ihre Bedeutung nicht verloren, sondern werden als effiziente wissensbasierte Systeme immer wichtiger. Denn intelligente Systeme der Zukunft müssen nicht nur in der Lage sein zu sagen, was sie entschieden haben, sondern auch wie sie zu dieser Entscheidung gekommen sind. Solche Systeme sind jedoch nur mit Hilfe von wissensbasierten Systemen auf der Grundlage von semantischen Technologien erreichbar. Heute reichen die Anwendungen von semantischen Systemen von der semantischen Suche, Knowledge Graphs, Chatbots, NLP, in der Medizin bis zur Telekommunikation, Verwaltung und Robotik. Semantische Technologien werden spätestens mit dem Voranschreiten des Internet of Things (IoT) und Industrie 4.0 Anwendungen allgegenwärtig sein. Dies ist unumgänglich, denn ohne sie ist auch die Interoperabilität unter Maschinen und insbesondere unter Roboter für eine intelligente Zusammenarbeit und Produktion nicht so einfach umsetzbar. Dafür gibt es bereits heute zahlreiche Beispiele aus der Industrie.DIPL.-ING. BÖRTEÇIN EGE studierte Informatik an der Technischen Universität Wien. Er beschäftigt sich seit 2005 mit Semantic Web und Künstlicher Intelligenz. Im Jahr 2007 gründete er eine Arbeitsgruppe, die sich mit Semantic Web-Technologien beschäftigt. Zudem ist er einer der Ersten im deutschsprachigen Raum, der Trainings über die Semantic Web Technologien angeboten hat. Nach langjährigen beruflichen Erfahrungen in verschiedenen Firmen und Konzernen als Software-Entwickler brachte er im Jahr 2015 mit zwei Kollegen gemeinsam sein erstes Buch Corporate Semantic Web beim Springer-Verlag heraus. Er ist Autor auch von zahlreichen populärwissenschaftlichen Beiträgen.PROF. DR. ADRIAN PASCHKE leitet seit 2008 die Corporate Semantic Web Gruppe an der Freien Universität Berlin und seit 2015 das Data Analytics Center (DANA) am Fraunhofer Institut für Offene Kommunikationssystem (FOKUS). Er hat aktiv in der Standardisierung semantischer Technologien im W3C, OMG, OASIS, RuleML und mit seinen wissenschaftlichen Publikation in der Corporate Semantic Web Community-Bildung beigetragen, sowie eine Vielzahl an Veranstaltungen wie das Berlin Semantic Web Meetup, RuleML, SWAT4LS, Semantics, Pragmatic Web organisiert.Neuronale Netze.-Deep Learning.-Machine Learning.-Semantische Künstliche Intelligenz.-Ontologien.-Corporate Smart Insights.-Knowledge Graphs.-Semantische Interoperabilität in Cyber-physischen Produktionssystemen.-Einsatz von Semantischen Technologien bei Unbemannten Systemen, Flugsicherung und Lieferkettenbeobachtung.-Die Rolle von Ontologien in NLP.-Artificial General Intelligence.-Bitcoin und Blockchain Technologien.-Semiotik.-Maschinenethik.-Welches Land macht das Rennen in Künstlicher Intelligenz?.

Game Theory and Machine Learning for Cyber Security
Move beyond the foundations of machine learning and game theory in cyber security to the latest research in this cutting-edge field In Game Theory and Machine Learning for Cyber Security, a team of expert security researchers delivers a collection of central research contributions from both machine learning and game theory applicable to cybersecurity. The distinguished editors have included resources that address open research questions in game theory and machine learning applied to cyber security systems and examine the strengths and limitations of current game theoretic models for cyber security. Readers will explore the vulnerabilities of traditional machine learning algorithms and how they can be mitigated in an adversarial machine learning approach. The book offers a comprehensive suite of solutions to a broad range of technical issues in applying game theory and machine learning to solve cyber security challenges. Beginning with an introduction to foundational concepts in game theory, machine learning, cyber security, and cyber deception, the editors provide readers with resources that discuss the latest in hypergames, behavioral game theory, adversarial machine learning, generative adversarial networks, and multi-agent reinforcement learning. Readers will also enjoy: A thorough introduction to game theory for cyber deception, including scalable algorithms for identifying stealthy attackers in a game theoretic framework, honeypot allocation over attack graphs, and behavioral games for cyber deceptionAn exploration of game theory for cyber security, including actionable game-theoretic adversarial intervention detection against advanced persistent threatsPractical discussions of adversarial machine learning for cyber security, including adversarial machine learning in 5G security and machine learning-driven fault injection in cyber-physical systemsIn-depth examinations of generative models for cyber security Perfect for researchers, students, and experts in the fields of computer science and engineering, Game Theory and Machine Learning for Cyber Security is also an indispensable resource for industry professionals, military personnel, researchers, faculty, and students with an interest in cyber security. GAME THEORY AND MACHINE LEARNING FOR CYBER SECURITY Move beyond the foundations of machine learning and game theory in cyber security to the latest research in this cutting-edge field In Game Theory and Machine Learning for Cyber Security, a team of expert security researchers delivers a collection of central research contributions from both machine learning and game theory applicable to cybersecurity. The distinguished editors have included resources that address open research questions in game theory and machine learning applied to cyber security systems and examine the strengths and limitations of current game theoretic models for cyber security. Readers will explore the vulnerabilities of traditional machine learning algorithms and how they can be mitigated in an adversarial machine learning approach. The book offers a comprehensive suite of solutions to a broad range of technical issues in applying game theory and machine learning to solve cyber security challenges. Beginning with an introduction to foundational concepts in game theory, machine learning, cyber security, and cyber deception, the editors provide readers with resources that discuss the latest in hypergames, behavioral game theory, adversarial machine learning, generative adversarial networks, and multi-agent reinforcement learning. Readers will also enjoy: A thorough introduction to game theory for cyber deception, including scalable algorithms for identifying stealthy attackers in a game theoretic framework, honeypot allocation over attack graphs, and behavioral games for cyber deceptionAn exploration of game theory for cyber security, including actionable game-theoretic adversarial intervention detection against advanced persistent threatsPractical discussions of adversarial machine learning for cyber security, including adversarial machine learning in 5G security and machine learning-driven fault injection in cyber-physical systemsIn-depth examinations of generative models for cyber security Perfect for researchers, students, and experts in the fields of computer science and engineering, Game Theory and Machine Learning for Cyber Security is also an indispensable resource for industry professionals, military personnel, researchers, faculty, and students with an interest in cyber security. Charles A. Kamhoua, PhD, is a researcher at the United States Army Research Laboratory’s Network Security Branch. He is co-editor of Assured Cloud Computing (2018) and Blockchain for Distributed Systems Security (2019), and Modeling and Design of Secure Internet of Things (2020). Christopher D. Kiekintveld, PhD, is Associate Professor at the University of Texas at El Paso. He is Director of Graduate Programs with the Computer Science Department. Fei Fang, PhD, is Assistant Professor in the Institute for Software Research at the School of Computer Science at Carnegie Mellon University. Quanyan Zhu, PhD, is Associate Professor in the Department of Electrical and Computer Engineering at New York University.

Enabling Healthcare 4.0 for Pandemics
ENABLING HEALTHCARE 4.0 FOR PANDEMICSTHE BOOK EXPLORES THE ROLE AND SCOPE OF AI, MACHINE LEARNING AND OTHER CURRENT TECHNOLOGIES TO HANDLE PANDEMICS.In this timely book, the editors explore the current state of practice in Healthcare 4.0 and provide a roadmap for harnessing artificial intelligence, machine learning, and Internet of Things, as well as other modern cognitive technologies, to aid in dealing with the various aspects of an emergency pandemic outbreak. There is a need to improvise healthcare systems with the intervention of modern computing and data management platforms to increase the reliability of human processes and life expectancy. There is an urgent need to come up with smart IoT-based systems which can aid in the detection, prevention and cure of these pandemics with more precision. There are a lot of challenges to overcome but this book proposes a new approach to organize the technological warfare for tackling future pandemics. In this book, the reader will find:* State-of-the-art technological advancements in pandemic management;* AI and ML-based identification and forecasting of pandemic spread;* Smart IoT-based ecosystem for pandemic scenario.AUDIENCEThe book will be used by researchers and practitioners in computer science, artificial intelligence, bioinformatics, data scientists, biomedical statisticians, as well as industry professionals in disaster and pandemic management. ABHINAV JUNEJA PHD is Professor and Head of Computer Science & Information Technology Department, at KIET Group of Institutions, Ghaziabad, Delhi-NCR, India. He has published more than 40 research articles.VIKRAM BALI PHD is Professor and Head of Computer Science and Engineering Department at JSS Academy of Technical Education, Noida, India. SAPNA JUNEJA PHD is Professor and Head of Computer Science Department at IMS Engineering College, Ghaziabad, India. VISHAL JAIN PHD is an Associate Professor in the Department of Computer Science and Engineering, Sharda University, Greater Noida, India. He has published more than 85 research articles and authored/edited more than 15 books. PRASHANT TYAGI, MBBS MS MCH is a practicing plastic surgeon at Cosmplastik Clinic,Sonepat, Delhi-NCR,India. Preface xvPART 1: MACHINE LEARNING FOR HANDLING COVID-19 11 COVID-19 AND MACHINE LEARNING APPROACHES TO DEAL WITH THE PANDEMIC 3Sapna Juneja, Abhinav Juneja, Vikram Bali and Vishal Jain1.1 Introduction 31.1.1 COVID-19 and its Various Transmission Stages Depending Upon the Severity of the Problem 41.2 COVID-19 Diagnosis in Patients Using Machine Learning 51.2.1 Machine Learning to Identify the People who are at More Risk of COVID-19 61.2.2 Machine Learning to Speed Up Drug Development 71.2.3 Machine Learning for Re-Use of Existing Drugs in Treating COVID-19 81.3 AI and Machine Learning as a Support System for Robotic System and Drones 101.3.1 AI-Based Location Tracking of COVID-19 Patients 101.3.2 Increased Number of Screenings Using AI Approach 111.3.3 Artificial Intelligence in Management of Resources During COVID-19 111.3.4 Influence of AI on Manufacturing Industry During COVID-19 111.3.5 Artificial Intelligence and Mental Health in COVID-19 141.3.6 Can AI Replace the Human Brain Intelligence in COVID-19 Crisis? 141.3.7 Advantages and Disadvantages of AI in Post COVID Era 151.4 Conclusion 17References 172 HEALTHCARE SYSTEM 4.0 PERSPECTIVES ON COVID-19 PANDEMIC 21Rehab A. Rayan, Imran Zafar and Iryna B. Romash2.1 Introduction 222.2 Key Techniques of HCS 4.0 for COVID-19 242.2.1 Artificial Intelligence (AI) 242.2.2 The Internet of Things (IoT) 252.2.3 Big Data 252.2.4 Virtual Reality (VR) 262.2.5 Holography 262.2.6 Cloud Computing 272.2.7 Autonomous Robots 272.2.8 3D Scanning 282.2.9 3D Printing Technology 282.2.10 Biosensors 292.3 Real World Applications of HCS 4.0 for COVID-19 292.4 Opportunities and Limitations 332.5 Future Perspectives 342.6 Conclusion 34References 353 ANALYSIS AND PREDICTION ON COVID-19 USING MACHINE LEARNING TECHNIQUES 39Supriya Raheja and Shaswata Datta3.1 Introduction 393.2 Literature Review 403.3 Types of Machine Learning 423.4 Machine Learning Algorithms 433.4.1 Linear Regression 433.4.2 Logistic Regression 453.4.3 K-NN or K Nearest Neighbor 463.4.4 Decision Tree 473.4.5 Random Forest 483.5 Analysis and Prediction of COVID-19 Data 483.5.1 Methodology Adopted 493.6 Analysis Using Machine Learning Models 543.6.1 Splitting of Data into Training and Testing Data Set 543.6.2 Training of Machine Learning Models 543.6.3 Calculating the Score 543.7 Conclusion & Future Scope 55References 554 RAPID FORECASTING OF PANDEMIC OUTBREAK USING MACHINE LEARNING 59Sujata Chauhan, Madan Singh and Puneet Garg4.1 Introduction 604.2 Effect of COVID-19 on Different Sections of Society 614.2.1 Effect of COVID-19 on Mental Health of Elder People 614.2.2 Effect of COVID-19 on our Environment 614.2.3 Effect of COVID-19 on International Allies and Healthcare 624.2.4 Therapeutic Approaches Adopted by Different Countries to Combat COVID-19 634.2.5 Effect of COVID-19 on Labor Migrants 634.2.6 Impact of COVID-19 on our Economy 644.3 Definition and Types of Machine Learning 644.3.1 Machine Learning & Its Types 654.3.2 Applications of Machine Learning 684.4 Machine Learning Approaches for COVID-19 694.4.1 Enabling Organizations to Regulate and Scale 694.4.2 Understanding About COVID-19 Infections 694.4.3 Gearing Up Study and Finding Treatments 694.4.4 Predicting Treatment and Healing Outcomes 704.4.5 Testing Patients and Diagnosing COVID-19 70References 715 RAPID FORECASTING OF PANDEMIC OUTBREAK USING MACHINE LEARNING: THE CASE OF COVID-19 75Nishant Jha and Deepak Prashar5.1 Introduction 765.2 Related Work 785.3 Suggested Methodology 795.4 Models in Epidemiology 805.4.1 Bayesian Inference Models 815.4.1.1 Markov Chain (MCMC) Algorithm 825.5 Particle Filtering Algorithm 825.6 MCM Model Implementation 835.6.1 Reproduction Number 845.7 Diagnosis of COVID-19 855.7.1 Predicting Outbreaks Through Social Media Analysis 865.7.1.1 Risk of New Pandemics 875.8 Conclusion 88References 88PART 2: EMERGING TECHNOLOGIES TO DEAL WITH COVID-19 916 EMERGING TECHNOLOGIES FOR HANDLING PANDEMIC CHALLENGES 93D. Karthika and K. Kalaiselvi6.1 Introduction 946.2 Technological Strategies to Support Society During the Pandemic 956.2.1 Online Shopping and Robot Deliveries 966.2.2 Digital and Contactless Payments 966.2.3 Remote Work 976.2.4 Telehealth 976.2.5 Online Entertainment 986.2.6 Supply Chain 4.0 986.2.7 3D Printing 986.2.8 Rapid Detection 996.2.9 QRT-PCR 996.2.10 Immunodiagnostic Test (Rapid Antibody Test) 996.2.11 Work From Home 1006.2.12 Distance Learning 1006.2.13 Surveillance 1006.3 Feasible Prospective Technologies in Controlling the Pandemic 1016.3.1 Robotics and Drones 1016.3.2 5G and Information and Communications Technology (ICT) 1016.3.3 Portable Applications 1016.4 Coronavirus Pandemic: Emerging Technologies That Tackle Key Challenges 1026.4.1 Remote Healthcare 1026.4.2 Prevention Measures 1036.4.3 Diagnostic Solutions 1036.4.4 Hospital Care 1046.4.5 Public Safety During Pandemic 1046.4.6 Industry Adapting to the Lockdown 1056.4.7 Cities Adapting to the Lockdown 1056.4.8 Individuals Adapting to the Lockdown 1066.5 The Golden Age of Drone Delivery 1076.5.1 The Early Adopters are Winning 1076.5.2 The Golden Age Will Require Collaboration and Drive 1086.5.3 Standardization and Data Sharing Through the Smart City Network 1086.5.4 The Procedure of AI and Non-AI-Based Applications 1106.6 Technology Helps Pandemic Management 1116.6.1 Tracking People With Facial Recognition and Big Data 1116.6.2 Contactless Movement and Deliveries Through Autonomous Vehicles, Drones, and Robots 1126.6.3 Technology Supported Temperature Monitoring 1126.6.4 Remote Working Technologies to Support Social Distancing and Maintain Business Continuity 1126.7 Conclusion 113References 1137 UNFOLDING THE POTENTIAL OF IMPACTFUL EMERGING TECHNOLOGIES AMID COVID-19 117Nusrat Rouf, Aatif Kaisar Khan, Majid Bashir Malik, Akib Mohi Ud Din Khanday and Nadia Gul7.1 Introduction 1187.2 Review of Technologies Used During the Outbreak of Ebola and SARS 1207.2.1 Technological Strategies and Tools Used at the Time of SARS 1207.2.2 Technological Strategies and Tools Used at the Time of Ebola 1217.3 Emerging Technological Solutions to Mitigate the COVID-19 Crisis 1247.3.1 Artificial Intelligence 1247.3.1.1 Application of AI in Developed Countries 1277.3.1.2 Application of AI in Developing Countries 1287.3.2 IoT & Robotics 1297.3.2.1 Application of IoT and Robotics in Developed Countries 1307.3.2.2 Application of IoT and Robotics in Developing Countries 1317.3.3 Telemedicine 1317.3.3.1 Application of Telemedicine in Developed Countries 1327.3.3.2 Application of Telemedicine in Developing Countries 1337.3.4 Innovative Healthcare 1337.3.4.1 Application of Innovative Healthcare in Developed Countries 1347.3.4.2 Application of Innovative Healthcare in Developing Countries 1347.3.4.3 Application of Innovative Healthcare in the Least Developed Countries 1357.3.5 Nanotechnology 1357.4 Conclusion 136References 1378 ADVANCES IN TECHNOLOGY: PREPAREDNESS FOR HANDLING PANDEMIC CHALLENGES 143Shweta Sinha and Vikas Thada8.1 Introduction 1438.2 Issues and Challenges Due to Pandemic 1458.2.1 Health Effect 1468.2.2 Economic Impact 1478.2.3 Social Impact 1488.3 Digital Technology and Pandemic 1498.3.1 Digital Healthcare 1498.3.2 Network and Connectivity 1518.3.3 Development of Potential Treatment 1518.3.4 Online Platform for Learning and Interaction 1528.3.5 Contactless Payment 1528.3.6 Entertainment 1528.4 Application of Technology for Handling Pandemic 1538.4.1 Technology for Preparedness and Response 1538.4.2 Machine Learning for Pandemic Forecast 1558.5 Challenges with Digital Healthcare 1578.6 Conclusion 158References 1599 EMERGING TECHNOLOGIES FOR COVID-19 163Rohit Anand, Nidhi Sindhwani, Avinash Saini and Shubham9.1 Introduction 1639.2 Related Work 1659.3 Technologies to Combat COVID-19 1669.3.1 Blockchain 1679.3.1.1 Challenges and Solutions 1689.3.2 Unmanned Aerial Vehicle (UAV) 1699.3.2.1 Challenges and Solutions 1699.3.3 Mobile APK 1709.3.3.1 Challenges and Solutions 1709.3.4 Wearable Sensing 1719.3.4.1 Challenges and Solutions 1729.3.5 Internet of Healthcare Things 1739.3.5.1 Challenges and Solutions 1759.3.6 Artificial Intelligence 1759.3.6.1 Challenges and Solutions 1759.3.7 5G 1769.3.7.1 Challenges and Solutions 1769.3.8 Virtual Reality 1769.3.8.1 Challenges and Solutions 1779.4 Comparison of Various Technologies to Combat COVID-19 1779.5 Conclusion 185References 18510 EMERGING TECHNIQUES FOR HANDLING PANDEMIC CHALLENGES 189Ankur Gupta and Puneet Garg10.1 Introduction to Pandemic 19010.1.1 How Pandemic Spreads? 19010.1.2 Background History 19110.1.3 Corona 19210.2 Technique Used to Handle Pandemic Challenges 19410.2.1 Smart Techniques in Cities 19410.2.2 Smart Technologies in Western Democracies 19610.2.3 Techno- or Human-Driven Approach 19710.3 Working Process of Techniques 19710.4 Data Analysis 20110.5 Rapid Development Structure 20610.6 Conclusion & Future Scope 207References 208PART 3: ALGORITHMIC TECHNIQUES FOR HANDLING PANDEMIC 21111 A HYBRID METAHEURISTIC ALGORITHM FOR INTELLIGENT NURSE SCHEDULING 213Tan Nhat Pham and Son Vu Truong Dao11.1 Introduction 21311.2 Methodology 21411.2.1 Data Collection 21411.2.2 Mathematical Model Development 21511.2.3 Proposed Hybrid Adaptive PSO-GWO (APGWO) Algorithm 21711.2.4 Discrete Version of APGWO 21911.2.4.1 Population Initialization 21911.2.4.2 Discrete Search Operator for PSO Main Loop 22311.2.4.3 Discrete Search Strategy for GWO Nested Loop 22411.2.4.4 Constraint Handling 23011.3 Computational Results 23011.4 Conclusion 232References 23312 MULTI-PURPOSE ROBOTIC SENSING DEVICE FOR HEALTHCARE SERVICES 237HirakRanjan Das, Dinesh Bhatia, Ajan Patowary and Animesh Mishra12.1 Introduction 23812.2 Background and Objectives 23812.3 The Functioning of Multi-Purpose Robot 23912.4 Discussion and Conclusions 248References 24913 PREVALENCE OF INTERNET OF THINGS IN PANDEMIC 251Rishita Khurana and Madhulika Bhatia13.1 Introduction 25213.2 What is IoT? 25513.2.1 History of IoT 25513.2.2 Background of IoT for COVID-19 Pandemic 25613.2.3 Operations Involved in IoT for COVID-19 25713.2.4 How is IoT Helping in Overcoming the Difficult Phase of COVID-19? 25713.3 Various Models Proposed for Managing a Pandemic Like COVID-19 Using IoT 26013.3.1 Smart Disease Surveillance Based on Internet of Things 26113.3.1.1 Smart Disease Surveillance 26113.3.2 IoT PCR for Spread Disease Monitoring and Controlling 26313.4 Global Technological Developments to Overcome Cases of COVID-19 26413.4.1 Noteworthy Applications of IoT for COVID-19 Pandemic 26513.4.2 Key Benefits of Using IoT in COVID-19 26913.4.3 A Last Word About Industrial Maintenance and IoT 27013.4.4 Issues Faced While Implementing IoT in COVID-19 Pandemic 27013.5 Results & Discussions 27013.6 Conclusion 271References 27214 MATHEMATICAL INSIGHT OF COVID-19 INFECTION—A MODELING APPROACH 275Komal Arora, Pooja Khurana, Deepak Kumar and Bhanu Sharma14.1 Introduction 27514.1.1 A Brief on Coronaviruses 27614.2 Epidemiology and Etiology 27714.3 Transmission of Infection and Available Treatments 27814.4 COVID-19 Infection and Immune Responses 27914.5 Mathematical Modeling 28014.5.1 Simple Mathematical Models 28114.5.1.1 Basic Model 28114.5.1.2 Logistic Model 28214.5.2 Differential Equations Models 28314.5.2.1 Temporal Model (Linear Differential Equation Model, Logistic Model) 28314.5.2.2 SIR Model 28414.5.2.3 SEIR Model 28514.5.2.4 Improved SEIR Model 28714.5.3 Stochastic Models 28814.5.3.1 Basic Model 28814.5.3.2 Simple Stochastic SI Model 28914.5.3.3 SIR Stochastic Differential Equations 29014.5.3.4 SIR Continuous Time Markov Chain 29014.5.3.5 Stochastic SIR Model 29114.5.3.6 Stochastic SIR With Demography 29214.6 Conclusion 292References 29315 MACHINE LEARNING: A TOOL TO COMBAT COVID-19 299Shakti Arora, Vijay Anant Athavale and Tanvi Singh15.1 Introduction 30015.1.1 Recent Survey and Analysis 30115.2 Our Contribution 30315.3 State-Wise Data Set and Analysis 30715.4 Neural Network 30815.4.1 M5P Model Tree 30915.5 Results and Discussion 30915.6 Conclusion 31415.7 Future Scope 314References 314Index 317

Computational Intelligence and Healthcare Informatics
COMPUTATIONAL INTELLIGENCE AND HEALTHCARE INFORMATICSTHE BOOK PROVIDES THE STATE-OF-THE-ART INNOVATION, RESEARCH, DESIGN, AND IMPLEMENTS METHODOLOGICAL AND ALGORITHMIC SOLUTIONS TO DATA PROCESSING PROBLEMS, DESIGNING AND ANALYSING EVOLVING TRENDS IN HEALTH INFORMATICS, INTELLIGENT DISEASE PREDICTION, AND COMPUTER-AIDED DIAGNOSIS. Computational intelligence (CI) refers to the ability of computers to accomplish tasks that are normally completed by intelligent beings such as humans and animals. With the rapid advance of technology, artificial intelligence (AI) techniques are being effectively used in the fields of health to improve the efficiency of treatments, avoid the risk of false diagnoses, make therapeutic decisions, and predict the outcome in many clinical scenarios. Modern health treatments are faced with the challenge of acquiring, analyzing and applying the large amount of knowledge necessary to solve complex problems. Computational intelligence in healthcare mainly uses computer techniques to perform clinical diagnoses and suggest treatments. In the present scenario of computing, CI tools present adaptive mechanisms that permit the understanding of data in difficult and changing environments. The desired results of CI technologies profit medical fields by assembling patients with the same types of diseases or fitness problems so that healthcare facilities can provide effectual treatments. This book starts with the fundamentals of computer intelligence and the techniques and procedures associated with it. Contained in this book are state-of-the-art methods of computational intelligence and other allied techniques used in the healthcare system, as well as advances in different CI methods that will confront the problem of effective data analysis and storage faced by healthcare institutions. The objective of this book is to provide researchers with a platform encompassing state-of-the-art innovations; research and design; implementation of methodological and algorithmic solutions to data processing problems; and the design and analysis of evolving trends in health informatics, intelligent disease prediction and computer-aided diagnosis. AUDIENCE The book is of interest to artificial intelligence and biomedical scientists, researchers, engineers and students in various settings such as pharmaceutical & biotechnology companies, virtual assistants developing companies, medical imaging & diagnostics centers, wearable device designers, healthcare assistance robot manufacturers, precision medicine testers, hospital management, and researchers working in healthcare system. OM PRAKASH JENA PHD is an assistant professor in the Department of Computer Science, Ravenshaw University, Cuttack, Odisha, India. He has more than 30 research articles in peer-reviewed journals and 4 patents.ALOK RANJAN TRIPATHY PHD is an assistant professor in the Department of Computer Science, Ravenshaw University, Cuttack, Odisha, India. AHMED A. ELNGAR PHD is an assistant professor of Computer Science, Chair of Scientific Innovation Research Group (SIRG), Director of Technological and Informatics Studies Center, at Beni-Suef University, Egypt. ZDZISLAW POLKOWSKI PHD is Professor in the Faculty of Technical Sciences, Jan Wyzykowski University, Polkowice, Poland. He has published more than 75 research articles in peer-reviewed journals. Preface xvPART I: INTRODUCTION 11 MACHINE LEARNING AND BIG DATA: AN APPROACH TOWARD BETTER HEALTHCARE SERVICES 3Nahid Sami and Asfia Aziz1.1 Introduction 31.2 Machine Learning in Healthcare 41.3 Machine Learning Algorithms 61.3.1 Supervised Learning 61.3.2 Unsupervised Learning 71.3.3 Semi-Supervised Learning 71.3.4 Reinforcement Learning 81.3.5 Deep Learning 81.4 Big Data in Healthcare 81.5 Application of Big Data in Healthcare 91.5.1 Electronic Health Records 91.5.2 Helping in Diagnostics 91.5.3 Preventive Medicine 101.5.4 Precision Medicine 101.5.5 Medical Research 101.5.6 Cost Reduction 101.5.7 Population Health 101.5.8 Telemedicine 101.5.9 Equipment Maintenance 111.5.10 Improved Operational Efficiency 111.5.11 Outbreak Prediction 111.6 Challenges for Big Data 111.7 Conclusion 11References 12PART II: MEDICAL DATA PROCESSING AND ANALYSIS 152 THORACIC IMAGE ANALYSIS USING DEEP LEARNING 17Rakhi Wajgi, Jitendra V. Tembhurne and Dipak Wajgi2.1 Introduction 182.2 Broad Overview of Research 192.2.1 Challenges 192.2.2 Performance Measuring Parameters 212.2.3 Availability of Datasets 212.3 Existing Models 232.4 Comparison of Existing Models 302.5 Summary 382.6 Conclusion and Future Scope 38References 393 FEATURE SELECTION AND MACHINE LEARNING MODELS FOR HIGH-DIMENSIONAL DATA: STATE-OF-THE-ART 43G. Manikandan and S. Abirami3.1 Introduction 433.1.1 Motivation of the Dimensionality Reduction 453.1.2 Feature Selection and Feature Extraction 463.1.3 Objectives of the Feature Selection 473.1.4 Feature Selection Process 473.2 Types of Feature Selection 483.2.1 Filter Methods 493.2.1.1 Correlation-Based Feature Selection 493.2.1.2 The Fast Correlation-Based Filter 503.2.1.3 The INTERACT Algorithm 513.2.1.4 ReliefF 513.2.1.5 Minimum Redundancy Maximum Relevance 523.2.2 Wrapper Methods 523.2.3 Embedded Methods 533.2.4 Hybrid Methods 543.3 Machine Learning and Deep Learning Models 553.3.1 Restricted Boltzmann Machine 553.3.2 Autoencoder 563.3.3 Convolutional Neural Networks 573.3.4 Recurrent Neural Network 583.4 Real-World Applications and Scenario of Feature Selection 583.4.1 Microarray 583.4.2 Intrusion Detection 593.4.3 Text Categorization 593.5 Conclusion 59References 604 A SMART WEB APPLICATION FOR SYMPTOM-BASED DISEASE DETECTION AND PREDICTION USING STATE-OF-THE-ART ML AND ANN MODELS 65Parvej Reja Saleh and Eeshankur Saikia4.1 Introduction 654.2 Literature Review 684.3 Dataset, EDA, and Data Processing 694.4 Machine Learning Algorithms 724.4.1 Multinomial Naïve Bayes Classifier 724.4.2 Support Vector Machine Classifier 724.4.3 Random Forest Classifier 734.4.4 K-Nearest Neighbor Classifier 744.4.5 Decision Tree Classifier 744.4.6 Logistic Regression Classifier 754.4.7 Multilayer Perceptron Classifier 764.5 Work Architecture 774.6 Conclusion 78References 795 CLASSIFICATION OF HEART SOUND SIGNALS USING TIME-FREQUENCY IMAGE TEXTURE FEATURES 81Sujata Vyas, Mukesh D. Patil and Gajanan K. Birajdar5.1 Introduction 815.1.1 Motivation 825.2 Related Work 835.3 Theoretical Background 845.3.1 Pre-Processing Techniques 845.3.2 Spectrogram Generation 855.3.2 Feature Extraction 885.3.4 Feature Selection 905.3.5 Support Vector Machine 915.4 Proposed Algorithm 915.5 Experimental Results 925.5.1 Database 925.5.2 Evaluation Metrics 945.5.3 Confusion Matrix 945.5.4 Results and Discussions 945.6 Conclusion 96References 996 IMPROVING MULTI-LABEL CLASSIFICATION IN PROTOTYPE SELECTION SCENARIO 103Himanshu Suyal and Avtar Singh6.1 Introduction 1036.2 Related Work 1056.3 Methodology 1066.3.1 Experiments and Evaluation 1086.4 Performance Evaluation 1086.5 Experiment Data Set 1096.6 Experiment Results 1106.7 Conclusion 117References 1177 A MACHINE LEARNING–BASED INTELLIGENT COMPUTATIONAL FRAMEWORK FOR THE PREDICTION OF DIABETES DISEASE 121Maqsood Hayat, Yar Muhammad and Muhammad Tahir7.1 Introduction 1217.2 Materials and Methods 1237.2.1 Dataset 1237.2.2 Proposed Framework for Diabetes System 1247.2.3 Pre-Processing of Data 1247.3 Machine Learning Classification Hypotheses 1247.3.1 K-Nearest Neighbor 1247.3.2 Decision Tree 1257.3.3 Random Forest 1267.3.4 Logistic Regression 1267.3.5 Naïve Bayes 1267.3.6 Support Vector Machine 1267.3.7 Adaptive Boosting 1267.3.8 Extra-Tree Classifier 1277.4 Classifier Validation Method 1277.4.1 K-Fold Cross-Validation Technique 1277.5 Performance Evaluation Metrics 1277.6 Results and Discussion 1297.6.1 Performance of All Classifiers Using 5-Fold CV Method 1297.6.2 Performance of All Classifiers Using the 7-Fold Cross-Validation Method 1317.6.3 Performance of All Classifiers Using 10-Fold CV Method 1337.7 Conclusion 137References 1378 HYPERPARAMETER TUNING OF ENSEMBLE CLASSIFIERS USING GRID SEARCH AND RANDOM SEARCH FOR PREDICTION OF HEART DISEASE 139Dhilsath Fathima M. and S. Justin Samuel8.1 Introduction 1408.2 Related Work 1408.3 Proposed Method 1428.3.1 Dataset Description 1438.3.2 Ensemble Learners for Classification Modeling 1448.3.2.1 Bagging Ensemble Learners 1458.3.2.2 Boosting Ensemble Learner 1478.3.3 Hyperparameter Tuning of Ensemble Learners 1518.3.3.1 Grid Search Algorithm 1518.3.3.2 Random Search Algorithm 1528.4 Experimental Outcomes and Analyses 1538.4.1 Characteristics of UCI Heart Disease Dataset 1538.4.2 Experimental Result of Ensemble Learners and Performance Comparison 1548.4.3 Analysis of Experimental Result 1548.5 Conclusion 157References 1579 COMPUTATIONAL INTELLIGENCE AND HEALTHCARE INFORMATICS PART III—RECENT DEVELOPMENT AND ADVANCED METHODOLOGIES 159Sankar Pariserum Perumal, Ganapathy Sannasi, Santhosh Kumar S.V.N. and Kannan Arputharaj9.1 Introduction: Simulation in Healthcare 1609.2 Need for a Healthcare Simulation Process 1609.3 Types of Healthcare Simulations 1619.4 AI in Healthcare Simulation 1639.4.1 Machine Learning Models in Healthcare Simulation 1639.4.1.1 Machine Learning Model for Post-Surgical Risk Prediction 1639.4.2 Deep Learning Models in Healthcare Simulation 1699.4.2.1 Bi-LSTM–Based Surgical Participant Prediction Model 1709.5 Conclusion 174References 17410 WOLFRAM’S CELLULAR AUTOMATA MODEL IN HEALTH INFORMATICS 179Sutapa Sarkar and Mousumi Saha10.1 Introduction 17910.2 Cellular Automata 18110.3 Application of Cellular Automata in Health Science 18310.4 Cellular Automata in Health Informatics 18410.5 Health Informatics–Deep Learning–Cellular Automata 19010.6 Conclusion 191References 191PART III: MACHINE LEARNING AND COVID PROSPECTIVE 19311 COVID-19: CLASSIFICATION OF COUNTRIES FOR ANALYSIS AND PREDICTION OF GLOBAL NOVEL CORONA VIRUS INFECTIONS DISEASE USING DATA MINING TECHNIQUES 195Sachin Kamley, Shailesh Jaloree, R.S. Thakur and Kapil Saxena11.1 Introduction 19511.2 Literature Review 19611.3 Data Pre-Processing 19711.4 Proposed Methodologies 19811.4.1 Simple Linear Regression 19811.4.2 Association Rule Mining 20211.4.3 Back Propagation Neural Network 20311.5 Experimental Results 20411.6 Conclusion and Future Scopes 211References 21212 SENTIMENT ANALYSIS ON SOCIAL MEDIA FOR EMOTIONAL PREDICTION DURING COVID-19 PANDEMIC USING EFFICIENT MACHINE LEARNING APPROACH 215Sivanantham Kalimuthu12.1 Introduction 21512.2 Literature Review 21812.3 System Design 22212.3.1 Extracting Feature With WMAR 22412.4 Result and Discussion 22912.5 Conclusion 232References 23213 PRIMARY HEALTHCARE MODEL FOR REMOTE AREA USING SELF-ORGANIZING MAP NETWORK 235Sayan Das and Jaya Sil13.1 Introduction 23613.2 Background Details and Literature Review 23913.2.1 Fuzzy Set 23913.2.2 Self-Organizing Mapping 23913.3 Methodology 24013.3.1 Severity_Factor of Patient 24413.3.2 Clustering by Self-Organizing Mapping 24913.4 Results and Discussion 25013.5 Conclusion 252References 25214 FACE MASK DETECTION IN REAL-TIME VIDEO STREAM USING DEEP LEARNING 255Alok Negi and Krishan Kumar14.1 Introduction 25614.2 Related Work 25714.3 Proposed Work 25814.3.1 Dataset Description 25814.3.2 Data Pre-Processing and Augmentation 25814.3.3 VGG19 Architecture and Implementation 25914.3.4 Face Mask Detection From Real-Time Video Stream 26114.4 Results and Evaluation 26214.5 Conclusion 267References 26715 A COMPUTATIONAL INTELLIGENCE APPROACH FOR SKIN DISEASE IDENTIFICATION USING MACHINE/DEEP LEARNING ALGORITHMS 269Swathi Jamjala Narayanan, Pranav Raj Jaiswal, Ariyan Chowdhury, Amitha Maria Joseph and Saurabh Ambar15.1 Introduction 27015.2 Research Problem Statements 27415.3 Dataset Description 27415.4 Machine Learning Technique Used for Skin Disease Identification 27615.4.1 Logistic Regression 27715.4.1.1 Logistic Regression Assumption 27715.4.1.2 Logistic Sigmoid Function 27715.4.1.3 Cost Function and Gradient Descent 27815.4.2 SVM 27915.4.3 Recurrent Neural Networks 28115.4.4 Decision Tree Classification Algorithm 28315.4.5 CNN 28615.4.6 Random Forest 28815.5 Result and Analysis 29015.6 Conclusion 291References 29116 ASYMPTOTIC PATIENTS’ HEALTHCARE MONITORING AND IDENTIFICATION OF HEALTH AILMENTS IN POST COVID-19 SCENARIO 297Pushan K.R. Dutta, Akshay Vinayak and Simran Kumari16.1 Introduction 29816.1.1 Motivation 29816.1.2 Contributions 29916.1.3 Paper Organization 29916.1.4 System Model Problem Formulation 29916.1.5 Proposed Methodology 30016.2 Material Properties and Design Specifications 30116.2.1 Hardware Components 30116.2.1.1 Microcontroller 30116.2.1.2 ESP8266 Wi-Fi Shield 30116.2.2 Sensors 30116.2.2.1 Temperature Sensor (LM 35) 30116.2.2.2 ECG Sensor (AD8232) 30116.2.2.3 Pulse Sensor 30116.2.2.4 GPS Module (NEO 6M V2) 30216.2.2.5 Gyroscope (GY-521) 30216.2.3 Software Components 30216.2.3.1 Arduino Software 30216.2.3.2 MySQL Database 30216.2.3.3 Wireless Communication 30216.3 Experimental Methods and Materials 30316.3.1 Simulation Environment 30316.3.1.1 System Hardware 30316.3.1.2 Connection and Circuitry 30416.3.1.3 Protocols Used 30616.3.1.4 Libraries Used 30716.4 Simulation Results 30716.5 Conclusion 31016.6 Abbreviations and Acronyms 310References 31117 COVID-19 DETECTION SYSTEM USING CELLULAR AUTOMATA–BASED SEGMENTATION TECHNIQUES 313Rupashri Barik, M. Nazma B. J. Naskar and Sarbajyoti Mallik17.1 Introduction 31317.2 Literature Survey 31417.2.1 Cellular Automata 31517.2.2 Image Segmentation 31617.2.3 Deep Learning Techniques 31617.3 Proposed Methodology 31717.4 Results and Discussion 32017.5 Conclusion 322References 32218 INTERESTING PATTERNS FROM COVID-19 DATASET USING GRAPH-BASED STATISTICAL ANALYSIS FOR PREVENTIVE MEASURES 325Abhilash C. B. and Kavi Mahesh18.1 Introduction 32618.2 Methods 32618.2.1 Data 32618.3 GSA Model: Graph-Based Statistical Analysis 32718.4 Graph-Based Analysis 32918.4.1 Modeling Your Data as a Graph 32918.4.2 RDF for Knowledge Graph 33118.4.3 Knowledge Graph Representation 33118.4.4 RDF Triple for KaTrace 33318.4.5 Cipher Query Operation on Knowledge Graph 33518.4.5.1 Inter-District Travel 33518.4.5.2 Patient 653 Spread Analysis 33618.4.5.3 Spread Analysis Using Parent-Child Relationships 33718.4.5.4 Delhi Congregation Attended the Patient’s Analysis 33918.5 Machine Learning Techniques 33918.5.1 Apriori Algorithm 33918.5.2 Decision Tree Classifier 34118.5.3 System Generated Facts on Pandas 34318.5.4 Time Series Model 34518.6 Exploratory Data Analysis 34618.6.1 Statistical Inference 34718.7 Conclusion 35618.8 Limitations 356Acknowledgments 356Abbreviations 357References 357PART IV: PROSPECTIVE OF COMPUTATIONAL INTELLIGENCE IN HEALTHCARE 35919 CONCEPTUALIZING TOMORROW’S HEALTHCARE THROUGH DIGITIZATION 361Riddhi Chatterjee, Ratula Ray, Satya Ranjan Dash and Om Prakash Jena19.1 Introduction 36119.2 Importance of IoMT in Healthcare 36219.3 Case Study I: An Integrated Telemedicine Platform in Wake of the COVID-19 Crisis 36319.3.1 Introduction to the Case Study 36319.3.2 Merits 36319.3.3 Proposed Design 36319.3.3.1 Homecare 36319.3.3.2 Healthcare Provider 36519.3.3.3 Community 36719.4 Case Study II: A Smart Sleep Detection System to Track the Sleeping Pattern in Patients Suffering From Sleep Apnea 37119.4.1 Introduction to the Case Study 37119.4.2 Proposed Design 37319.5 Future of Smart Healthcare 37519.6 Conclusion 375References 37520 DOMAIN ADAPTATION OF PARTS OF SPEECH ANNOTATORS IN HINDI BIOMEDICAL CORPUS: AN NLP APPROACH 377Pitambar Behera and Om Prakash Jena20.1 Introduction 37720.1.1 COVID-19 Pandemic Situation 37820.1.2 Salient Characteristics of Biomedical Corpus 37820.2 Review of Related Literature 37920.2.1 Biomedical NLP Research 37920.2.2 Domain Adaptation 37920.2.3 POS Tagging in Hindi 38020.3 Scope and Objectives 38020.3.1 Research Questions 38020.3.2 Research Problem 38020.3.3 Objectives 38120.4 Methodological Design 38120.4.1 Method of Data Collection 38120.4.2 Method of Data Annotation 38120.4.2.1 The BIS Tagset 38120.4.2.2 ILCI Semi-Automated Annotation Tool 38220.4.2.3 IA Agreement 38320.4.3 Method of Data Analysis 38320.4.3.1 The Theory of Support Vector Machines 38420.4.3.2 Experimental Setup 38420.5 Evaluation 38520.5.1 Error Analysis 38620.5.2 Fleiss’ Kappa 38820.6 Issues 38820.7 Conclusion and Future Work 388Acknowledgements 389References 38921 APPLICATION OF NATURAL LANGUAGE PROCESSING IN HEALTHCARE 393Khushi Roy, Subhra Debdas, Sayantan Kundu, Shalini Chouhan, Shivangi Mohanty and Biswarup Biswas21.1 Introduction 39321.2 Evolution of Natural Language Processing 39521.3 Outline of NLP in Medical Management 39621.4 Levels of Natural Language Processing in Healthcare 39721.5 Opportunities and Challenges From a Clinical Perspective 39921.5.1 Application of Natural Language Processing in the Field of Medical Health Records 39921.5.2 Using Natural Language Processing for Large-Sample Clinical Research 40021.6 Openings and Difficulties From a Natural Language Processing Point of View 40121.6.1 Methods for Developing Shareable Data 40121.6.2 Intrinsic Evaluation and Representation Levels 40221.6.3 Beyond Electronic Health Record Data 40321.7 Actionable Guidance and Directions for the Future 40321.8 Conclusion 406References 406Index 409

Evaluation of Some Android Emulators and Installation of Android OS on Virtualbox and VMware
An Android emulator is an Android Virtual Device (AVD) that represents a specific Android device. You can use an Android emulator as a target platform to run and test your Android applications on your PC. The Android Emulator runs the Android operating system in a virtual machine called an Android Virtual Device (AVD). The AVD contains the full Android software stack, and it runs as if it were on a physical device.You can also install Android on VMware Workstation, VMware Player, VMware ESXi, and Virtualbox. Once you install Android on VMware Workstation or ESXi, you will get all features available for Android installed on a smartphone.This report covers the evaluation of some Android Emulators and Installation of Android OS on Virtualbox and VMware. The report contains the following sections:1. Enabling Hardware Virtualization2. General guideline for installing OpenGL and running OpenGL programs on Microsoft Windows 7 and higher3. Apk Downloader from Google Play Store to PC4. How to install Xapk applications5. Smart GaGa Android Emulator6. NoxPlayer Android Emulator7. Other Types of Gaming Android Emulators8. Genymotion Android Emulator9. Installing Android x86 ISO using Virtualbox10. Installing Android x86 ISO using VMware11. Running Android Apps on Google Chrome using ARC Welder extensionI am Dr. Hidaia Mahmoud Mohamed Alassouli. I completed my PhD degree in Electrical Engineering from Czech Technical University by February 2003, and my M. Sc. degree in Electrical Engineering from Bahrain University by June 1995. I completed also one study year of most important courses in telecommunication and computer engineering courses in Islamic university in Gaza. So, I covered most important subjects in Electrical Engineering, Computer Engineering and Telecommunications Engineering during my study. My nationality is Palestinian from gaza strip.I obtained a lot of certified courses in MCSE, SPSS, Cisco (CCNA), A+, Linux.I worked as Electrical, Telecommunicating and Computer Engineer in a lot of institutions. I worked also as a computer networking administrator.I had considerable undergraduate teaching experience in several types of courses in many universities. I handled teaching the most important subjects in Electrical and Telecommunication and Computer Engineering.I could publish a lot of papers a top-tier journals and conference proceedings, besides I published a lot of books in Publishing and Distribution houses.I wrote a lot of important Arabic articles on online news websites. I also have my own magazine website that I publish on it all my articles: http:// www.anticorruption.000space.comMy personal website: www.hidaia-alassouli.000space.comEmail: hidaia_alassouli@hotmail.com

Programming Basics
Explore the basics of the three most popular programming languages: C#, Java, and Python and see what it's like to function in today's world from the perspective of a programmer. This book's uses is highly practical approach with numerous code listings aimed at bringing generations together through the intricacies of technology.You'll learn how understanding the basics of coding benefits non-programmers working with software developers. Those in the gaming/media industry will also benefit from understanding a programmer's point of view. The same applies to software testers and even company executives, who might have an education in business instead of computer science.WHAT YOU'LL LEARN* Think and read code-listings like a programmer* Gain a basic working proficiency in three popular programming languages* Communicate more efficiently with programmers of all experience levels in a work-based environment* Review advanced OOP concepts such as exceptions and error handling* Set up your programming environments for Windows, MacOS, and LinuxWHO THIS BOOK IS FORThose looking to discover programming, including beginners in all fields, and professionals looking to understand how code works.Robert Ciesla is an author and filmmaker from Helsinki, Finland. He is also a freelance-programmer working mostly in the indie game scene. He is the author of Encryption for Organizations and Individuals (2020), Game Development with Ren'Py (2019) and Mostly Codeless Game Development (2017).Chapter 1. Why kids love to code (and you will too)* Motivation for and the benefits of programming* The basic hardware components of a computerChapter 2. What is programming? (and what does it take)* Basic programming concepts explained with some specifics for C#, Java, and Python* What an integrated development environment (IDE) refers to* The gist of variables, variable manipulation, and flow control logicChapter 3. Setting up your programming environments for Windows, MacOS, and LinuxChapter 4. Object-Oriented Programming (OOP)* The object-oriented programming paradigm explained in detail* The basics of UMLChapter 5. File Operations, Multithreading, and Other Wonders of Java* Small tutorials for the language demonstrating the more advanced mechanics of the languageChapter 6. And now for something completely different: Python* More Python techniques (file operations etc.)Chapter 7. C#: A jack of most programming tasks* Deploying C# for desktop, online, and mobile platformsChapter 8. Advanced OOP Techniques* Advanced OOP concepts: exceptions, error handling, etc.Chapter 9. Unified Modeling Language (UML)* Detailed techniques (class relationships and multiplicity, etc.)* Software tools for modeling in UML
